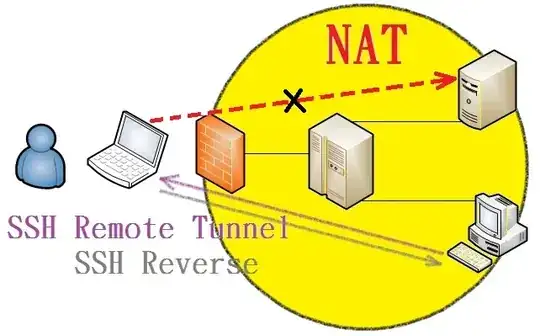
We have an IP address on the global internet: "A"
We only have access to "A".
We have a network behind a router that does NAT: 192.168.1.0/24
There is a client behind that NAT: "B"
We don't have access to "B" and the "NAT" router.
Goal: reach the "B" directly with "A".
We cannot use port forwarding or UPnP, etc.
Question: what is the trick to reach "B"? A trick that could be avoided if the router had a stateful firewall, not just NAT!
We are thinking that when "B" browses the web, it will go out to the internet. When it is receiving replies, the router that does the NAT needs to decide which NATed IP did "B" have? (there could be more machines behind the NATed network). For this the NAT router uses the port information too. Maybe if we/they are using UDP, we can try all non-privileged ports with the IP "A" to send a packet to "B"?
The NAT router is just a simply soho router. (original problem: trying to prove that NAT is not a firewall, but we need an evidence for it)