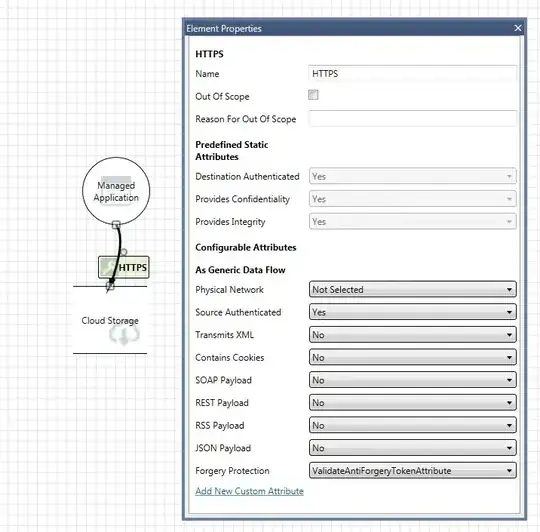
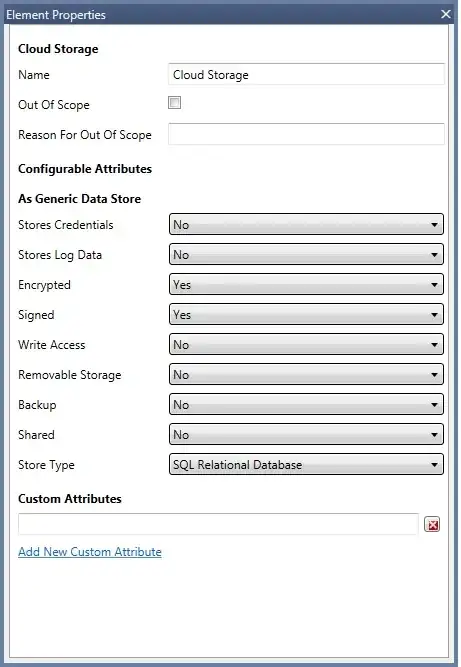
I have a threat model with a Cloud Storage entity an Managed Application which accesses it. Here is the diagram:
The Microsoft Threat Modeling Tool says in the report that:
Cloud Storage may be spoofed by an attacker and this may lead to data being written to the attacker's target instead of Cloud Storage. Consider using a standard authentication mechanism to identify the destination data store.
Why is that? In an HTTPS connection the destination is always authenticated (see element properties) What setting should I modify to get rid of this threat?