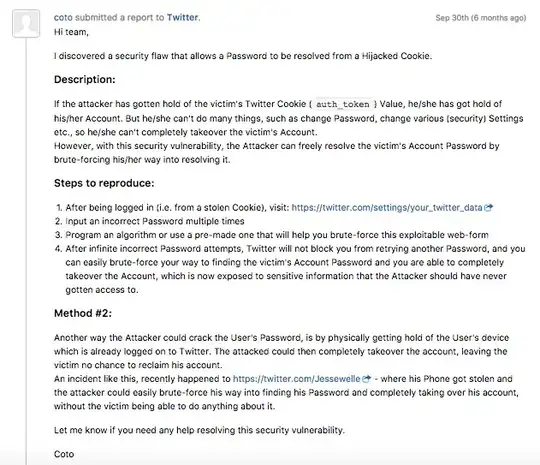
I recently discovered and reported a security vulnerability to Twitter:
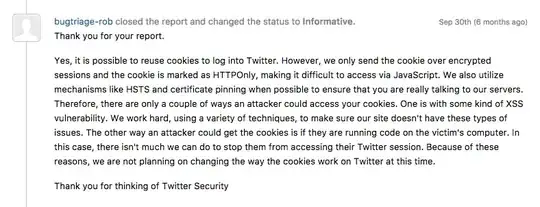
Despite my belief that the report it indeed valid, they replied to me with the following response:
As far as I can tell, this security engineer is talking about protection against cookie hijacking. However that is not my concern at all. My concern is that you can completely takeover a Twitter Account of a user as long as you have the value of his auth_token cookie.
No, I don't claim Twitter has a security flaw leaving sensitive cookie values exposed. There are tons of ways a cookie can be hijacked, and that already puts the victim-user into a dangerous position. However, he can reset his password etc. at any time. But when the attacker is able to brute-force his way into obtaining the password of the logged-in user, hence taking full control of the account (changing email, passwords, etc.), the victim has absolutely no chance of getting his account back.
I even made a video to demonstrate how easy the attack is.
Do you think this vulnerability is valid/critical? Am I or the security engineer at Twitter "wrong"?