I am trying to figure out if NTLMv2 is vulnerable to a reflection attack. I cannot find a citation that clearly states NTLMv2 as being vulnerable. NTLMv1 is horribly insecure so there really is not point in even discussing the security of NTLMv1. No client should initiate NTLMv1 and no server should accept it.
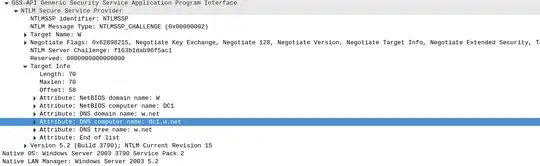
The reason I have doubts is that NTLMv2 has "Target Information" that includes the name of the server the client is initiating to. Here is a screenshot of this Target Info from a typical NTLMv2 over HTTP authentication:
If an attacker tried to reuse this challenge by sending it back to the server over a separate authentication instance, the server could clearly see the target information was simply not correct. And you can't change the target information because it's factored into final token so the hash would come out wrong.
So can some explain to me precisely how a reflection attack would work with NTLMv2?
UPDATE:
Ok, then let's talk about this "SMB Relay Attack" which several people have mentioned. I am interested in any NTLMv2 exploit.
Specifically, the links posted by markgamache are not clear about NTLMv2. It does not explain the precise mechanism. Yes, a man-in-the-middle is easy with the NTLMv1 NTLMSSP_AUTH hash (not to be confused with the password equivalent hash obtained from something like meterpreter> hashdump). But NTLMv2 is different. It was specifically designed to thwart MITM types of attacks. My understanding is that it uses the "Target Info" block which contains the "DNS computer name" and "NetBIOS computer name" of the target (see screenshot above). This block of data is factored into the computation of the NTLMSS_AUTH hash. Therefore I would think that either the client or the server would detect if this information is incorrect (with or without signing).
Unfortunately it seems like a lot of the documented exploits are 90% about NTLMv1 and then they just casually claim that NTLMv2 is equally vulnerable without providing the details. It makes me wonder if they are mixing up unrelated concepts. For example, if an attacker obtains the raw password equivalent hashes, they can be used with NTLMv1 or NTLMv2. But of course this requires either Administrative credentials (to insert code into lsass.exe to dump passwords) or brute force NTLMSSP_AUTH hashes which is difficult.
UPDATE 2:
After a lot of web searching, I think this link (provided indirectly by atdre) is the best description of the Reflection / Relay issue which are largely the same:
Protecting Privileged Domain Accounts: Network Authentication In-Depth
Regarding the Target Information block, I can only conclude that clients simply do not try to verify that the name matches the target for whatever reason.