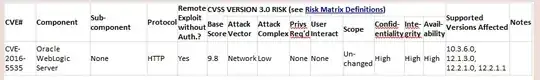
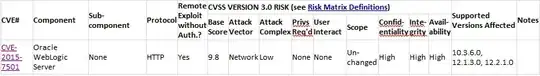
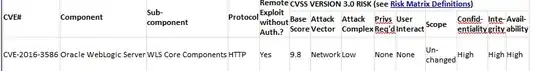
According to Oracle website, following deserialization vulnerabilities are related to HTTP protocol.
CVE-2015-7501, CVE-2016-5535, CVE-2016-3586, CVE-2016-3510, etc.
But I do not understand why Weblogic says it is related to HTTP protocol.
Unless the server application expect a serialized java object as input through HTTP protocol, is there any other possible way to exploit these vulnerabilities?