I am testing a .net based application running on a Win2012r2 server providing a http-based web services and relying on windows's SChannel for implementing tls1.2 mutual authentication against tls1.2 only capable clients.
Mutual authentication has been working so far very nicely (client certificate are properly validated against the list of trusted issuers defined and active on the local computer certificate store).
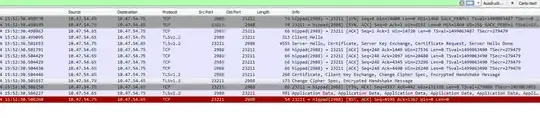
Yesterday I came across the following scenario that somehow puzzles me: even if the client is presenting a certificate length of 0, the handshake seems to be technically successful and does not result in an Handshake Failure or an Handshake alert:
- (on server side) Server Hello, Certificate, Server Key Exchange, Certificate Request, Server Hello Done;
- (on client side) Certificate, Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message (however the test client is not providing any client certificate - client certificate length of 0 - during the handshake);
- (on server side): change cipher spec, Encrypted Handshake message;
Why is the Server side not terminating the handshake (Handshake failure or alert) after getting no client certificate ?
Could it just be the way that wireshark is interpreting / parsing the handshake process ?
Is this something configurable / tunable at SChannel level or can only be adjusted at application level ?