A similar point has been answered on Wireshark's own SO/SE in How to interpret signal strength. Yet we can add some more details here. And add some up to date links since the ones on that answer died.
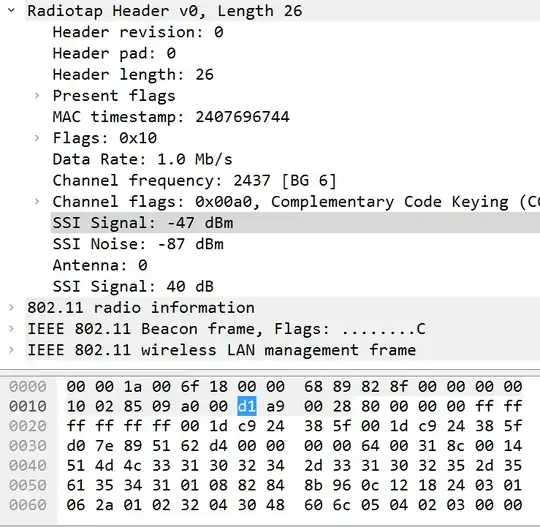
The SSI Signal is radiotap's antena signal (and the SSI noise is the antenna noise) and we see in there:
RF signal power at the antenna. This field contains a single signed 8-bit value, which indicates the RF signal power at the antenna, in decibels difference from 1mW.
*(emphasis mine)
Borrowing from the answer on wireshark's SO we have:
10((dBm-30)/10) Watts
So, yeah, that pretty much is signal power. But note that that is:
What your card is telling you, radiotap is an encapsulation, not something that actually went through the air. Therefore:
the sniffing network adapter received the packet or it represents the power at which a nearby AP (access point) received this packet?
It is the sniffing adapter/card/antenna.
Not the strength of the signal for the packet it is the strength of the signal at the time that the packet was received. Now, as we saw in the radiotap quote above, it is the power at the antenna. But note that there is also noise there (SSI noise). I'm not particularly confident that:
SSI Signal - SSI Noise = Actual power that the *packet* was received
This is because you have Signal to Noise Ratio, and some of the noise could have been interpreted as part of the signal. SNR is beyond me though.
In summary, radiotap is the encapsulation of the state of your network card and antenna at the time that the packet was received. Whether that can be used as an estimate of AP signal strength is debatable. Since the signal strength is the signal of the network that the card is retrieving packets from and the rest is (more-or-less) noise then you can use that as an estimate.
In laboratory conditions I'd argue that the signal strength presented in the radiotap is a good enough estimate of signal AP strength discounted the distance from the AP. Yet, in the real world, e.g. in an urban area with a lot of APs and interference, the radiotap signal strength is neigh useless to tell you anything about an AP.
Extra
Also note that the radiotap encapsulation is part of IEEE 802.11 and is defacto standard for captured wireless packets. Calling it a header is an oversimplification. There is a header that defines several fields that may be present or not and then there is a list of fields that a certain card may or may not provide (but should tell you which ones are provided through the header). This can be analogous to TCP and TCP options.
For example, in the Linux kernel code you can find the definition of the header in include/net/ieee80211_radiotap.h. And then the structure that is built after the header in net/wireless/radiotap.c.
Some useful reading: