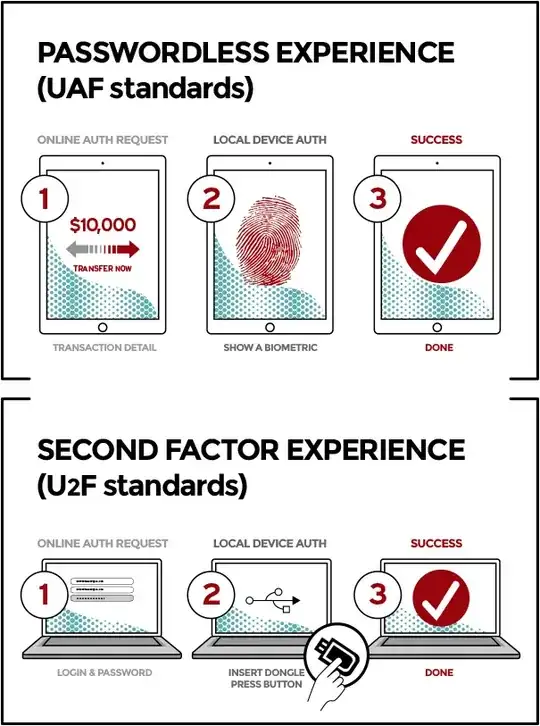
As you may already be aware, the Universal 2nd Factor (U2F) standard is a standard for 2nd-factor authentication which allows users to authenticate to web applications using a USB hardware token.
While reading up on this standard, I discovered that the Fast IDentity Online (FIDO) Alliance, which created the U2F standard, also has another standard they created around the same time called the Universal Authentication Framework (UAF), which seems very similar to U2F:
(Source)
These standards seem very similar, with the only significant difference being what authentication mechanism is used in step 2. However, further reading suggests that UAF allows for multiple different authentication mechanisms in step 2:
The passwordless FIDO experience is supported by the Universal Authentication Framework (UAF) protocol. In this experience, the user registers their device to the online service by selecting a local authentication mechanism such as swiping a finger, looking at the camera, speaking into the mic, entering a PIN, etc. The UAF protocol allows the service to select which mechanisms are presented to the user.
With this in mind, why is U2F even a separate standard from UAF in the first place? What's so different about U2F that warrants it being an entirely different standard rather than just another authentication mechanism for UAF?