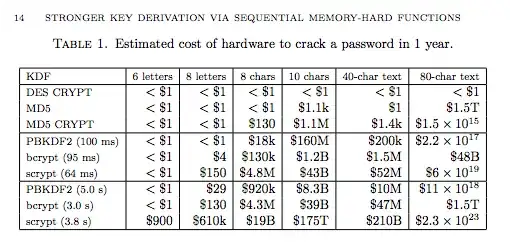
To understand the table it is worthwhile to read the article. The table is only an illustration and estimation for memory hard function. Furthermore, the article states:
We caution again that these values are very approximate and reflect only the
cost of the cryptographic circuitry with circa 2002 technology: It is quite possible
that the costs of other hardware (control circuitry, boards, power supplies) and
operating costs (power, cooling) would increase the costs by a factor of 10 above
these; and it is equally possible that improvements in semiconductor technology
and improved cryptographic circuit designs could each reduce the costs by a factor
of 10.
The price of computing power has dropped quite a bit; in 2003, the KAYSO cost $82 per gigaflops, in 2017, an AMD RX Vega 64 cost $0.03 per gigaflops (so a factor 2733). Granted that FLOPS is not a real measure for dealing with brute-force cryptography, but you should, for the costs take a factor 2500 into account.
Bitcoin miners could probably, with quite a lot of effort, be used to crack AES256 hashes, which are not in the table. But for the rest they're quite useless. You might, if you are determined, create your own ASIC for this. That may be quite costly to develop, but afterwards easier to distribute.
That also brings us to your probability calculation. They are a very gross simplification. Real values depend on the scalability of the algorithm (might not be linear) and a lot of other factors.
Look also at the development of new algorithms. For example: Andrey Bogdanov e.a. presented in 2011 a paper how to significantly reduce the cracking time of AES 128, 192 and 256 bit keys (Biclique Cryptanalysis of the Full AES).
From al that to the question if a password is safe is really a step too far. For passwords, there are a lot of other issues. Most passwords are cracked because they are relatively easy to guess (qwerty123) and/or are in dictionary files. On the other hand, if a cracking device does not have the encrypted password, it will be difficult to decrypt, so access to your (even encrypted) passwords must also be controlled.