The question , Setting up a fake AP - problem with iptables and DNS server , I posted before was answered and fixed, to not confuse people looking for the same problem in the future I wanted to post a new question that follows the problem I had but doesnt really have anything to do with it,since the former question was about my iptables and led to using a DNS server, this question is only about DNS and my hosts configuration or so I suspect, and the topic of this question is actually quite different.
I'm having some difficulty accessing websites using a bridged AP i made with aircrack-ng suite.
I cant access websites such as : yahoo, hotmail, google, CNN etc.. . But I can access several websites like facebook,youtube and addresss bar search with google engine works fine.
I have set my etc/dhcp/dhcpd.conf and my routing & IP tables entry as follows;
running iptables configuration and at0 routing rules(bash file):
#!/bin/sh
ifconfig at0 up
ifconfig at0 10.0.0.1 netmask 255.255.255.0
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
iptables -P FORWARD ACCEPT
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
iptables -t nat -A POSTROUTING -o wlan0 -j MASQUERADE
running DHCP server : /etc/init.d/isc-dhcp-server start
/etc/dhcp/dhcpd.conf file:
authoritative;
default-lease-time 600;
max-lease-time 7200;
subnet 10.0.0.0 netmask 255.255.255.0
{
option subnet-mask 255.255.255.0;
option domain-name "freewifi";
option routers 10.0.0.1;
option domain-name-servers 194.90.0.1;
range 10.0.0.10 10.0.0.20;
}
The DNS server im using is the best offered DNS server using NameBench.py.
I'm getting this message on google for example, and its the same for many more websites:
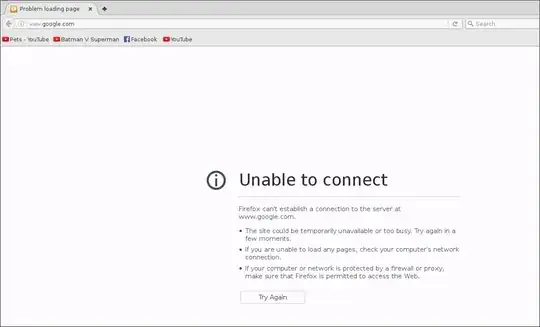
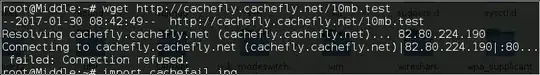
I can ping, but I cant apt-get or use wget, meaning I dont really have access to the internet(?)
Using Kali Linux, MTU is 1500 , my speed is 5Mb/s using wireless connection. What is the problem here?
- UPDATE
I am able to connect directly to websites that I couldnt before if I type in the address bar: https://www.yahoo.com but if its without https it says unable to connect.
I read somewhere that mozila only allows HTTPS connections or it could be the Kali forcing HTTPS to make it secure. On WireShark I see many TCP DUP ACK'S and RST'S.