I am researching SNMP and I read about a scanning tool from SANS called SNMPing. Is this tool still available?
I cannot find anywhere to download it. Sending an empty email to snmptool@sans.org just gets rejected.
I am researching SNMP and I read about a scanning tool from SANS called SNMPing. Is this tool still available?
I cannot find anywhere to download it. Sending an empty email to snmptool@sans.org just gets rejected.
I can't find a public source for SNMPing, but you might be more interested in more robust options. My personal favourite is onesixtyone. It pings, as well as brute-forces community strings (if you want to do that).
There is also snmpwalk and snmpenum which can read the information from the system.
All 3 of these tools are available on Backtrack, but if you are looking for Windows versions (as SNMPing was win32), you can find various parts of these tools here, but I cannot vouch for them.
I have no idea whether the tool you are looking for is still available for download, but I will try to point you to some SNMP scanning tools that are far more known than SNMPing.
When it comes to SNMP scanning tools, SNMPwalk and SNMPenum are references (both mentioned in another answer). However, I advice you to use Nmap to scan for SNMP-enabled hosts. Nmap is one of the most reputable network port scanners out there and is, at least for me, the most reliable way to scan for SNMP or any other active service. It is open source and you can download and use it for free.
Assuming that SNMP is running on port 161/UDP, which is default, the Nmap command to run an SNMP scan would be:
nmap -sU -p161 target-ip-range-or-host
If you want to get SNMP service version information, append -sV to the last command. Here is a sample output against a host which does not run SNMP on 161/UDP:
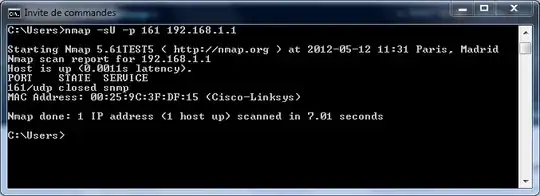
Using the Nmap Scrpting Engine, you can bruteforce SNMP community string, retrieve IOS configurations, enumerate Windows services, etc. The full list of Nmap's scripts is available here.