I'm putting together a demo of Ophcrack for my team here. It's been a while since I used it, like 7-10 years. Booting up into either the Ophcrack live CD or using it in Kali, I'm seeing samdump2 and pwdump showing the same SID/hash for all users of the machine (running in a VM) and Ophcrack says all accounts have an empty password. Any idea what's going on? Can Ophcrack/JTR be used against Windows 10?
-
4it's almost as if that's been updated by ms in the last 10 years, shocking... – dandavis Jan 19 '17 at 18:52
-
2Heh, @dandavis. That program never even got updated well enough to work to decode passwords on Win8. It says so on their web site. – SDsolar May 20 '17 at 09:23
3 Answers
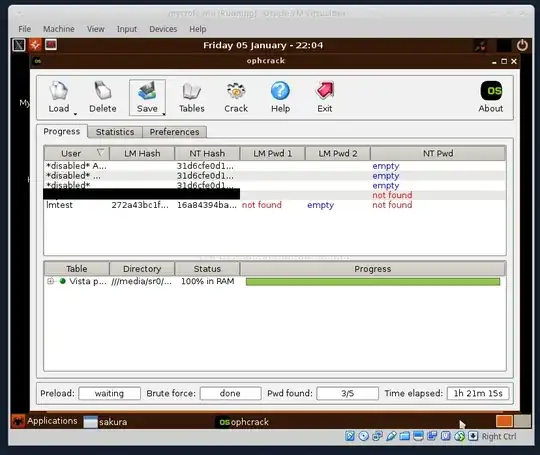
The Vista/7 Ophcrack will work on Windows 10 hashes. I've run it myself, against both NTLM and LM hashes.
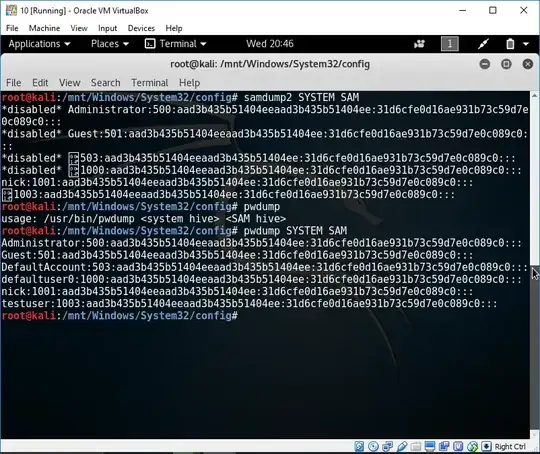
The only time that I've seen aad3b435b51404eeaad3b435b51404ee and 31d6cfe0d16ae931b73c59d7e0c089c0 is when the passwords are actually unset/empty/disabled. These are explicitly detected and marked as "empty" by Ophcrack:
It really does look as though the hashes that you found are classic empty hashes.
Once you get some non-empty hashes, Ophcrack should work fine.
(Side note: but it will only run the wordlists/tables that you feed it, which is somewhat limiting compared to modern capabilities. On modern systems with GPU, you can cover a lot more ground and have overall higher success rates with a full cracking suite like John the Ripper or hashcat. I would suggest demos of those also, to supplement your demo.)
- 9,128
- 1
- 31
- 55
-
2I wonder if the accounts in question being local accounts or not would make a difference. Can you remember whether the Windows 10 accounts you cracked Ophcrack with were local accounts, as opposed to accounts that required a Microsoft account? – Hashim Aziz May 11 '19 at 00:04
For some reason the tools detect "no password" but there is in fact the password hash shown.
Pwdump7 for instance states NO PASSWORD but the NTLM password hash is in the 3rd last field.
C:\Users\dark_st3alth\Desktop\pwdump7>PwDump7.exe
Pwdump v7.1 - raw password extractor
Author: Andres Tarasco Acuna
url: http://www.514.es
Administrator:500:NO PASSWORD*********************:878D8014606CDA29677A44EFA1353FC7:::
Guest:501:NO PASSWORD*********************:NO PASSWORD*********************:::
:503:NO PASSWORD*********************:NO PASSWORD*********************:::
dark_st3alth:1001:NO PASSWORD*********************:878D8014606CDA29677A44EFA1353FC7:::
Likewise, fgdump gives a similar NO PASSWORD output, but it fact the password is there:
C:\Users\dark_st3alth\Desktop\Release>fgdump.exe
fgDump 2.1.0 - fizzgig and the mighty group at foofus.net
Written to make j0m0kun's life just a bit easier
Copyright(C) 2008 fizzgig and foofus.net
fgdump comes with ABSOLUTELY NO WARRANTY!
This is free software, and you are welcome to redistribute it
under certain conditions; see the COPYING and README files for
more information.
No parameters specified, doing a local dump. Specify -? if you are looking for help.
--- Session ID: 2017-01-19-21-46-02 ---
Starting dump on 127.0.0.1
^C
Administrator:500:NO PASSWORD*********************:NO PASSWORD*********************:::
dark_st3alth:1001:NO PASSWORD*********************:878D8014606CDA29677A44EFA1353FC7:::
DefaultAccount:503:NO PASSWORD*********************:NO PASSWORD*********************:::
Guest:501:NO PASSWORD*********************:NO PASSWORD*********************:::
I've used the password "secret" for demonstrative purposes.
For local accounts nothing has changed, but for logins by Microsoft accounts, pins, and picture passwords, I can't be sure if hashes are in fact generated. This is something I haven't gotten around to testing.
- 3,052
- 8
- 23
-
There are Linux-based tools that work on Win8 and let you just delete passwords. Might want to search those out. They are boot disks like Ophcrack. No idea how they would act on Win10. – SDsolar May 20 '17 at 09:24
-
This is not the case with Ophcrack, or even similar tools that simply reset the password, which I'm also seeing the same errors in. To be an answer to this question, you should have tried an Ophcrack liveCD/USB and confirmed whether the result that you got in it was the same. – Hashim Aziz Oct 12 '18 at 23:24
Like Royce Williams said aad3b435b51404eeaad3b435b51404ee and 31d6cfe0d16ae931b73c59d7e0c089c0 are the LM and NTHash for no password respectively. You can double check it also here.
Besides that, it's always a good idea to google a hash first if you are in a pentest because this could sometimes already give the answer.
- 202
- 1
- 11