Recently, a vulnerability in Facebook's messenger app which allowed attacks to access a users private messages via cross-origin AJAX was patched and disclosed.
Simple Bug allows Hackers to Read all your Private Facebook Messenger Chats
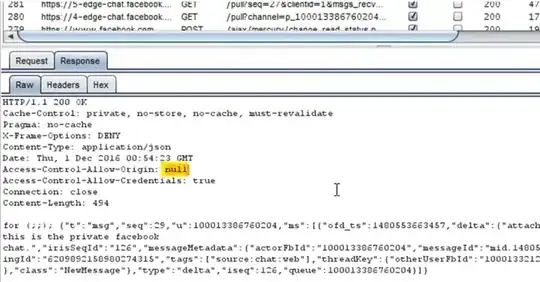
The root of this issue was misconfigured cross-origin header implementation on Facebook's chat server domain, which allowed an attacker to bypass origin checks and access Facebook messages from an external website.
The name of "Originull" and screenshot seem to indicate the problem is the following header:
Access-Control-Allow-Origin: null
But this leaves me wondering, how exactly a value of null leads to a vulnerability. This doesn't look like a valid origin, unless you were to somehow visit a website from the domain of null (actually, it would need to be http://null or https://null, as the protocol would need to be included).
I checked, and null is not actually an allowed value in the same way * is, in Chrome or Firefox.
XMLHttpRequest cannot load http://other.localhost/ajax.php. The 'Access-Control-Allow-Origin' header contains the invalid value 'null'. Origin 'http://localhost' is therefore not allowed access.
(Using a value of * does work however, so clearly just being null is not enough for arbitrary pages to access these resources.)
Is there some feature or bug in browsers that read null as *? Or some feature in browsers, like pages opened by a data URI, that allow matching to null? How does this vulnerability work?