I need to produce a presentation on buffer overflows for a college class. I managed to create a simple buffer overflow where i inject the address of a specific function on the EIP and the function gets executed as expected.
Then, i want to show the more interesting example where i inject shellcode that gets executed. That's when it stops working. I emulated the way people explained it on various websites, but it doesn't work.
Regardless of the shellcode i use (Shellcode), the issue is that the code i injected doesn't get executed. So the program jumps to the correct address, then stops without executing whatever is at the address.
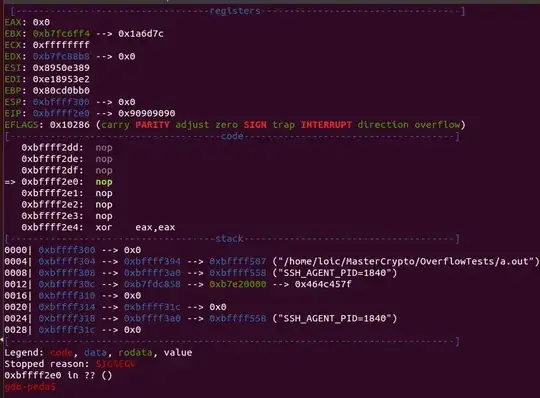
So as you may see in central section of the picture, named "code", the program accesses my nop sled, at address 0xbffff2e0 (shellcode starts 4 bytes below), but nothing happens.
Then, the error output says that it tried to access 0xbffff2e0 but couldn't find anything (see bottom of the image : "0xbffff2e0 in ?? ()" ).
Do you have an idea on what's happening?
What am i missing?
Edit : i'm adding the code used in this exercise, as asked
#include <stdio.h>
#include <string.h>
void secret(){
printf("This is a secret message : you are Awesome!\n");
}
void denied(){
printf("You don't have the permission to see the secret.\n");
}
int main(int argc, char *argv[]){
char buf[20];
strcpy(buf, argv[1]);
printf("%s\n",buf);
if(strcmp(buf, "myPassword") == 0){
secret();
}
else{
denied();
}
return 0;
}