Usability v/s Security Matrices isn't resolved with dependent
Biometric Authorization & Authentication
For example, before I start - have a look at how the basic foundation of security is built in matrices:
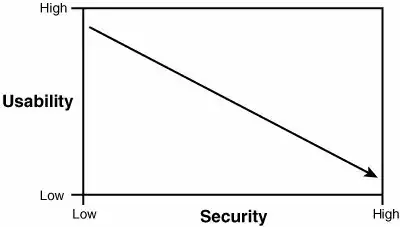
It can be easily concluded that High Security unfortunately comes with low usability features.
How Do I know This?
I have been in ongoing research on secure architectural implementation of possible authorization & authentication mechanisms using iOS & Android - both. The framework isn't decided & with all the research experience, I have nailed down few points here which might be worth noting down.

Possible Risks
- If it were to be primary security protection to access critical
assets, there are traders, who can knock off an individual in
person, chop off his thumb & login. It could be that simple for
those who have finance data kept in secure login (primary use case)
procedures.
- Other threats could involve having the print collected using high
resolution imaging & then apply image processing techniques to
collect clone of the thumbprint & use it later having it imprinted
on thin plastic filament. That way there is a second bypass possible
here.
- Materials used in building a phone might collect prints & afterwards
the specific part can be physically taken apart to have it cloned &
address security bypasses.
In contrary to using normal passwords, The latter - it could be in users mind solving the problem of physically not compromised. All it needs is user security level awareness of having the password & login strict to a compliant firm type e.g. PCI-DSS, etc (in cases of financial data fraud).
There's usability, but then there's security. Hence, more usability will lead to obvious broader security risk surfaces. Therefore, below is worth a consideration of using biometric devices such as the following:
- iris (L)
- termogram (L)
- DNA (L)
- smell (L)
- retina (L)
- veins [hand] (L)
- ear (M)
- walk (M)
- fingerprint (M)
- face (M)
- signature (H)
- palm (M)
- voice (H)
- typing (M)
Note: H for (High), M for (Medium) & L for (Low) risks.
Let's conceptualise the same in matrices as per basic construct mentioned earlier & see if it matches the criteria:
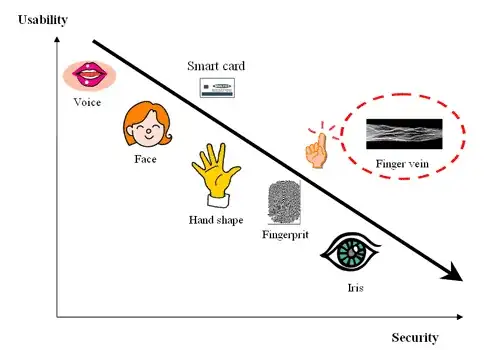
Overall Risks Factors:
The physical attack
Offer a clean glass of champagne to the target victim during a social
physical event, and manage to recover the glass to get a high
definition picture of the target fingerprints.
The storage attack
All these fingerprints have to be stored either locally or centrally.
Steal the Phone5 of the target victim and through physical interfaces
get the internal content and attack the stored and crypted
fingerprint. If they are stored centrally, since we aren't in the
magic space time where 0 probability live, this central storage will
get broken sooner or later.
The algorithmic attack
As any other authentication technic, fingerprint reading, storing and
comparing will use algorithms. Hence this authentication is also
exposed to algorithmic attacks.
The aforementioned methods have risks. There's an important point about biometric authentication that many of the commercial installations respect, but which is not immediately obvious: Banks should never rely on biometrics to supply both authentication and identification. Biometric measurements are useful, but they're in no wise unique. Two people may not have the exact same fingerprint, hand geometry, or iris patterns, but the measurements are often lossy enough to allow for collisions. Biometrics need to be just one part in a multi-factor authentication system & hence can be fit when 2FA & Biometric go side by side.
Other Usability Limitations:
Aside from these risks, other limitations include the following:
- Error rate - false accepts and false rejects are still unacceptably high for many types of biometrics.
- User acceptance - still not widely trusted by users; The various privacy concerns are still quite high, and the idea that a part of your body is now a security mechanism is still not relevant to some citizens.
OP's question compares the same with traditional password - hence traditional password schemes are less probable & have lesser exposure to threat surfaces than the prior Biometric Security Mechanisms. Using more compliant keeping the traditional passwords & biometric optional post prior login methods have been successful - might be the take-away.



