Today this article was published by the BBC: Talk Talk and Post Office routers hit by cyber-attack. It states:
It involves the use of a modified form of the Mirai worm - a type of malware that is spread via hijacked computers, which causes damage to equipment powered by the Linux operating system.
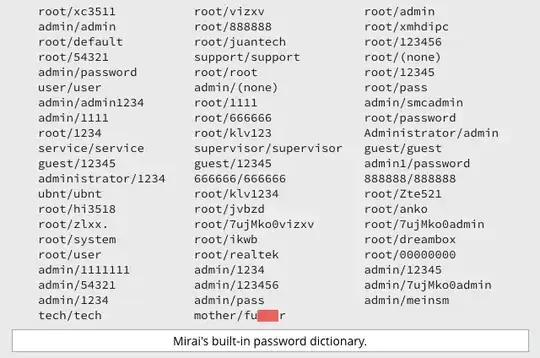
Reading wikipedia on the Mirai worm it states it works as following:
Mirai then identifies vulnerable IoT devices using a table of more than 60 common factory default usernames and passwords, and logs into them to infect them with the Mirai malware. Infected devices will continue to function normally, except for occasional sluggishness, and an increased use of bandwidth. A device remains infected until it is rebooted, which may involve simply turning the device off and after a short wait turning it back on. After a reboot, unless the login password is changed immediately, the device will be reinfected within minutes.
So my question is Can I protect my router from the Mirai Worm and How would I know if my router was vulnerable?