I was trying to use dnsspoof but it did not work as expected. These are the steps I followed:
- Set IP forward in kernel to 1
arpspoof -i eth0 -t 192.168.1.39 -r 192.168.1.1andarpspoof -i eth0 -t 192.168.1.1 -r 192.168.1.39. Checked witharp -aand it works- Create a file.txt with:
137.222.0.38 *.hello.com dnsspoof -i eth0 -f file.txt
From victim computer 192.168.1.39 I browse to www.hello.com and it is redirected to the real site. Output from dnsspoof is:
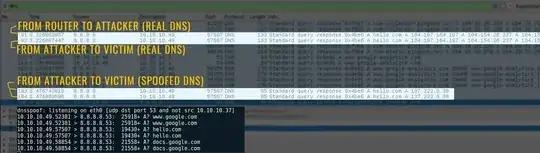
dnsspoof: listening on eth0 [udp dst port 53 and not src 192.168.1.35]
192.168.1.39.1113 > 8.8.8.8.53: 3864+ A? www.hello.com
192.168.1.39.1113 > 8.8.8.8.53: 3864+ A? www.hello.com
I have checked on Wireshark and it seems that the victim is receiving responses from the same IP with the router MAC (first) and with the attacker MAC (second). I have flushed the DNS and tried fresh requests, even though this should not be necessary in theory. My questions are:
1) Why is this not working? Someone has suggested using iptables to block packets from the router, but it seems strange that dnsspoof does not do it by itself, and none of the tutorials I have checked (1, 2, 3, 4) requires this step. Also, I cannot get the right iptables rule to make this work correctly.
2) Many tutorials seem to use dnsspoof without arpspoof. Is the latter really necessary? I mention because once (by chance) the DNS spoof seemed to work in another computer which was not "arpspoofed".
3) How does dnsspoof work? Just by listening for DNS requests in the whole LAN and then sending the resolution back?
EDIT
With the iptables command iptables -D FORWARD --match string --algo kmp --hex-string '|68 65 6c 6c 6f|' --jump DROP the router is not queried, and only the spoofed DNS is sent. However, the victim browser stays loading forever and finally it says it cannot access the site(?). Without the iptables command I am able to see how the request goes like this:
victim --> attacker --> router and answer: router --> attacker --> victim
And just after this the attacker sends twice the spoofed DNS to the victim. Again, I am still confused about this behaviour and have not answered yet any of my three questions. I kind of believe the answer for (2) is that dnsspoof spoofed the whole network, but only if you did arpspoof before you can guarantee that the spoofed packet will get to the victim before the legitimate one. However, in my case, this is not working because the petition is forwarded.
EDIT
This is a network capture with the same example over another network (10.10.10.0). The legitimate DNS is forwarded first and, later on, the spoofed DNS. In this example, there were other petitions in the middle of both responses but quite often I get the packets one after the other.