No, there's no way such a thing could possibly exist, for any significant amount of time.
There's two big hints at this in the article itself:
many technical experts are raising equally serious doubts about its feasibility
A Home Office spokesman said – “We have not issued any hardware or software specifications.
The only way this could work on a properly secured website is if either:
- The user cooperated with the surveillance
- The website cooperated with the government
- All the governments in the world decided to cooperate to surveil everyone
Obviously, there is still a high (but lowering) number of insecure websites. And telephony systems are completely insecure, from a cryptography perspective. However, the quoted example - Gmail - is about as secure as you can get.
In general, considering how much noise Snooper's Charter caused in security circles, even if there is such a "Black Box" being designed, it'll be useless long before it is actually used.
The reasons for this are a bit complex to understand, but read on if you're interested on the gory details
As other answers mention, the mechanism that you described resembles the well studied man-in-the-middle attack.
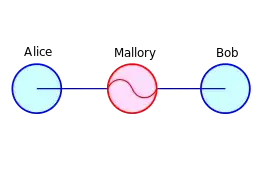 diagram by Miraceti
diagram by Miraceti
Let's see how it works in practice. Here, Alice (e.g.: the user) and Bob (e.g.: the website) want to communicate confidentially. They communicate through a communication medium that Mallory controls. Clearly, if the messages are not encrypted, Mallory can read and change any messages.
What happens if Alice and Bob use a properly secured channel, though?
- Mallory can't read the messages at all. This property is called confidentiality, and is usually provided by symmetric encryption.
- Mallory can't change the messages. This property is called integrity, and is usually provided by a message authentication code
- Mallory can, at most, prevent messages from being delivered.
Now comes the tricky part.
For all these mechanisms to work, Alice and Bob have to agree on a secret key - something resembling a long randomly generated password. Because Alice and Bob might not have communicated before, this is usually done through asymmetric cryptography.
Assume Alice and Bob never communicated before. How can they agree on a secret "password" to use, in a way that Mallory can't possibly learn it? Let's use an analogy with the old postal system:
- Alice sends a letter to Bob saying they want to communicate
- Bob receives the message, and sends Alice a package with a open padlock
- Alice receives the padlock, generates a "password", puts it inside a box, locks the box with the padlock, and sends the box to Bob
- Bob gets the locked box, unlocks it, and reads the "password".
Obviously, Mallory can't open the padlock without Bob's padlock key.
What Mallory can do, though, is intercept the padlock when Bob sends it to Alice, and replace it with a padlock of their own.
To prevent this easy attack, there is usually a trusted third party - let's call her Faythe. Faythe is responsible for "photographing" everyone's padlocks, and distributing these (very detailed) photographs. Because Alice trusts Faythe, she can check the padlock she receives against the photograph, and make sure it belongs to Bob.
In the web world, Faythe is called a Certificate Authority (CA), and the photographs are called certificates (technically, signed certificates).
Now it becomes clear how the government's plan might work:
because they can't force Alice (the user) or Bob (the website) to cooperate (in general), they can try to persuade Faythe (the CA) to "send" fake certificates to Alice.
Researchers in the security community are aware of this scenario, and there's several mechanisms to prevent it, both technical and social:
Shame CAs that do this. Although this sounds quite basic, it's extremely powerful. CAs are usually commercial entities. Their reputation, is, quite literally, their only asset. Once their reputation is ruined, they're essentially worthless. A CA that forged certificates would become distrusted very quickly. If Alice doesn't trust the CA anymore, the government attack would stop working.
Sanity check the certificate. In practice, certificates for a given website don't change often, and usually only at well defined intervals. If they change outside of the expected interval, you can assume the certificate is compromised. This technique is called certificate pinning.
Cross-check the certificate. Since a particular website's certificate remains constant globally, you can detect compromised CAs by cross-checking the certificates users receive across the world. There's several projects doing this, including Google's Certificate Transparency, EFF's SSL Observatory, MonkeySphere, Convergence, Perspectives, and probably others I'm not aware of.
Note that all of these mechanisms have been developed before any government even thought of publicly doing this.
Given all this knowledge, and assuming the worse possible case (a "blackbox" that works for a short period of time) - what can you do to protect yourself?
