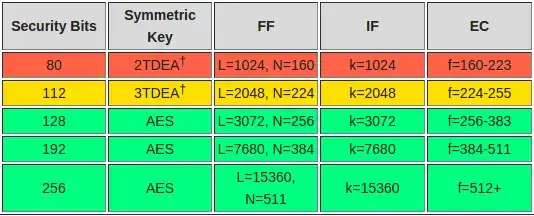
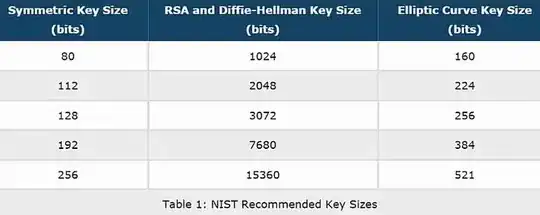
I am not of the field of IS but I want to secure my humble VPS and I cam across a clashing of opinions between 3 IS guys: 2 say that ed25519 ssh keys are a bit more secure than ssh-rsa of 4096 bytes and one says that in our era, there isn't a significant different at all and either will be just fine for me.
While I don't know who's "right", I went to do some limited reading (limited as I don't have the knowledge to fully understand every passage I read on the subject), and I found out by all that has to do with bytes, public ed25519 keys have much fewer bytes than public ssh-rsa 4096 keys, and hence their private keys are also much shorter.
My question can hence be comprised of the following two questions:
If so, and I'm sorry I think you I need to go and learn 6 months of cryptography --- How are these more secure? I am feeling there is another criterion for their alleged superiority here, and it's not just the amount ob bytes. It's something with formatting.
If it's is only formatting, couldn't we implement this formatting to ssh-rsa 4096 keys? I mean if ed25519 keys contain about 90% less bytes, and we implement their special formatting to ssh-rsa 4096 keys, couldn't we create the most powerful ssh public key ever until now?