Completely and permanently (unless you re-install it) disable Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability on Windows. These are components of the Intel Management Engine firmware. While Intel ME still runs, the Windows drivers are disabled and Intel ME can no longer access Windows.
1) Download the Intel Setup and Configuration Software (Intel SCS) and extract.
2) Open up an administrator command prompt and navigate to where you extracted the files in step 1
3) In the command prompt, run ACUConfig.exe UnConfigure. If you get an error, try one of the options below:
Unconfiguring a system in ACM without RCS integration:
ACUConfig.exe UnConfigure /AdminPassword <password> /Full
Unconfiguring a system with RCS integration:
ACUConfig.exe UnConfigure /RCSaddress <RCSaddress> /Full
4) Still in the command prompt, disable and/or remove LMS (Intel Management and Security Application Local Management Service):
sc config LMS start=disabledsc delete LMS- also run
sc qc LMS, which will either show you the path to LMS.exe or FAIL. If it shows you the path, use Explorer to delete it. If it FAILED, do not be concerned.
5) Reboot
6) Check if there is still a socket listening on the Intel ME Internet Assigned Names Authority (IANA) ports on the client: 16992, 16993, 16994, 16995, 623, and 664 (you can also do this before you start to verify it is listening. The Intel ME listens even if the Intel AMT GUI shows Intel ME is "Unconfigured")
- in a command prompt (does not need to be elevated), run
netstat -na | findstr "\<16993\> \<16992\> \<16994\> \<16995\> \<623\> \<664\>"
7) The Intel AMT GUI should now show "information unavailable on both remaining tabs" (you might have had 3 or more tabs before going thru the steps above)
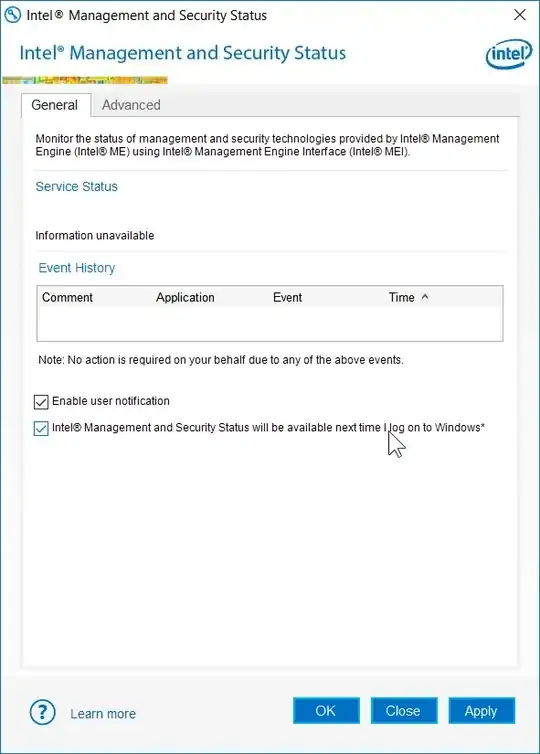
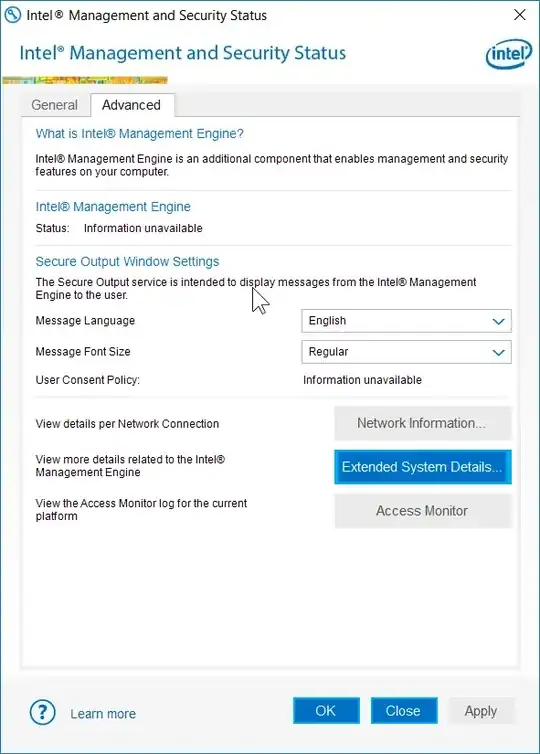
Voilá, you have gotten rid of Intel AMT. And you've done the right thing, especially after the 2017-05-01 privilege escalation issue.
From this source (disclaimer, it's my own blog)

