There are many materials about the Dictionary attack or bit-flipping attack to PPTP VPN. But is it possible to implement a downgrade attack to PPTP.
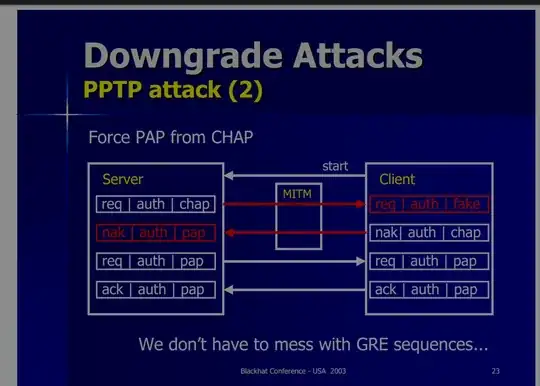
This is a picture showing how to implement a downgrade attack to PPTP (from https://www.blackhat.com/presentations/bh-usa-03/bh-us-03-ornaghi-valleri.pdf).
I've tried in this way, but doesn't work. And I got some wired results: if I change the configure-request packet form server to client, replacing its CHAP with PAP, and then I change the configure-request packet from client to server, adding a PAP option in it. The configuration process will never stop, server and client will get into a dead-lock loop, keep sending configure-request packets to each other.
After some research, I found out that: the MitM must send a Nak packet to server in order to reject the CHAP option. Maybe this Nak packet will terminate the dead-lock loop. But this will mess up the GRE sequence number of client, because this Nak packet is sent by MitM, and not the client.
Is there any other way to implement a downgrade attack on PPTP? I've stuck here for a very long time, and I'd appreciate any advice.