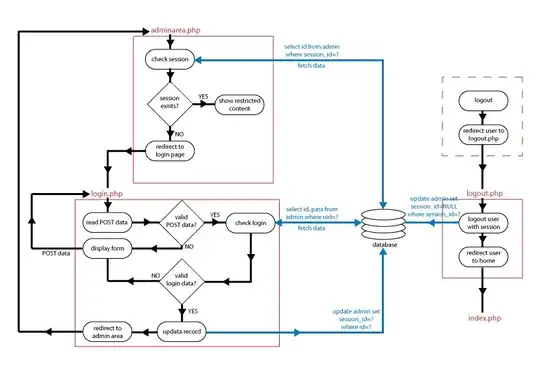
Don't implement your own session handler. Use $_SESSION, it was written and audited by people who very good understanding security. I don't even know the intricacies of how your session handler works, but based on the little information you have given us its insecure.
SQL Injection is useful to obtain data from the database. We HASH passwords because in the event of an attacker obtaining this data, they will be forced to crack the hash before its useful. However, in your case, it doesn't matter that you are vulnerable to CWE-257, the attacker can just pull the session id out of the database, and use that to authenticate.
I could also gain admin access because you have made no mention of OWASP a9 - Insufficient Transport Layer Protection. You are also vulnerable to Clickjacking, every web app is by default. CSRF or "session riding" was already mentioned.
Enable the security flags "httponly", "secure". You can do this for $_SESSION by configuring PHP.
A defense in depth strategy is to plan on failure and limit the access your administrator has. Don't allow file upload or code execution. This is the number 1 reason why Wordpress instances get hacked, once you have admin on a Wordpress site, you have remote code execution on the server. Wordpress also implemented their own session handler at one point, and you guessed it, it was very insecure.