In sum: Does Credential Guard make passing-the-hash and passing-the-ticket attacks effectively unavailable on networks of Windows 10 / Windows Server 2016 machines? If not, how do you still acquire hashes or tickets to pass?
From what I've learned about pen testing and malicious attacker methods over the couple of years that I've been studying them in earnest, one of the happiest discoveries that an offensive actor can make happens when penetrating a target's Windows network and finding that it is not properly configured & administered to resist pass-the-hash and/or pass-the-ticket attacks. In such situations, it often becomes disturbingly easy for the intruder to (using a tool like mimikatz) dump NTLM password hashes and Kerberos credentials that are contained in the memory or are on the disk of the foothold machine that was originally compromised and use them to successfully move laterally and breach other boxes on the network. In the best case, it's possible to sooner or later get your hands on the keys to the kingdom: an NTLM hash or Kerberos ticket for a Domain Administrator or Enterprise Administrator. And if that happens... the target is in a world of trouble.
Unfortunately for the offense, in Windows 8.1, Windows Server 2012 R2, Windows 10, and Windows Server 2016 Microsoft has implemented a number of measures to try to make passing-the-hash and passing-the-ticket attacks harder to pull off. The most ambitious of these is called Credential Guard, and arrived in Windows 10 Enterprise on the client and Windows Server 2016. The details of how Credential Guard appears to work technically are a little complicated. But at a high level things are more straightforward: Windows takes advantage of virtualization capabilities present in newer Intel and AMD processors to encase the credentials store that exists in memory on a Windows machine in a special kind of virtual machine. A virtual machine that (in theory) even a program that manages to get administrator/SYSTEM privileges on the OS cannot penetrate. Thus, as the pitch goes even if you manage to get your malware onto a PC, and even manage to elevate your privileges on that PC all the way to SYSTEM, if that PC has Credential Guard enabled on it and you try to use a tool like mimikatz to dump the credential store you will get nothing usable for passing-the-hash or passing-the-ticket.
In theory.
So let's say you're a pen tester facing a Windows domain that consists exclusively of Windows 10 Enterprise workstations, Windows Server 2016 servers, and a Windows Server 2016 domain controller. All running with Credential Guard enabled. If you'd like to use pass-the-hash or pass-the-ticket for lateral movement, are you just screwed? Aside from being able to dump the hashes & tickets in the credential store, what other methods might an attacker use to gain hashes or tickets that can be passed? Can you bypass or disable Credential Guard? Or are you faced with just giving up on passing hashes/tickets entirely and trying other ways to do lateral movement?
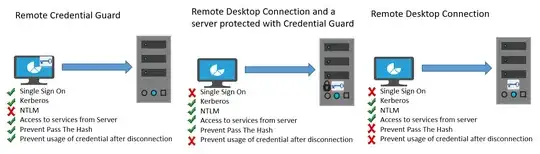
Edit: FYI, it turns out that in the July Windows 10 "Anniversary Update" Microsoft very quietly introduced Remote Credential Guard, which is apparently designed to prevent your credentials from ever being sent to the remote box when you initiate a Remote Desktop connection to it. (Same general idea as Restricted Admin mode for RDP, I guess, except improved.) A "helpful" diagram from MS: