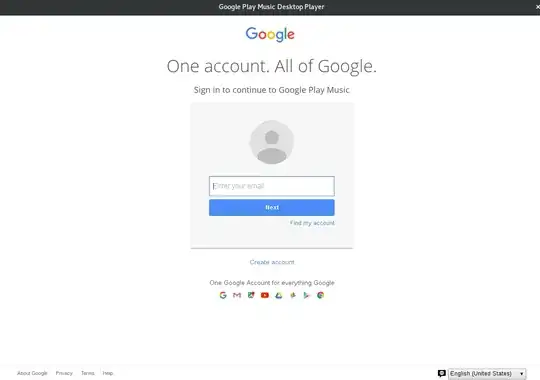
Here are some ways I can think of but if someone tried hard enough I don't think there would be a way to stop him.
Check a fake email - Google's login will only display a password input if the username exists so by entering any email you know does not exists (Ex: ajksjdlalsjdlkasldkldjalk@gmail.com) if the password box still shows up then it is not a genuine Google login page.
Try viewing the source - Since the app is pretty much a browser you might be able to view the source. Try right click and view source or F12.
Packet sniffer - Download a packet sniffer such as Wire Shark and check where the traffic is coming from. Is it from Google or from another source?
These are only a few examples but sadly there is no solid way I can think of. Be cautious and pay attention to anything abnormal.