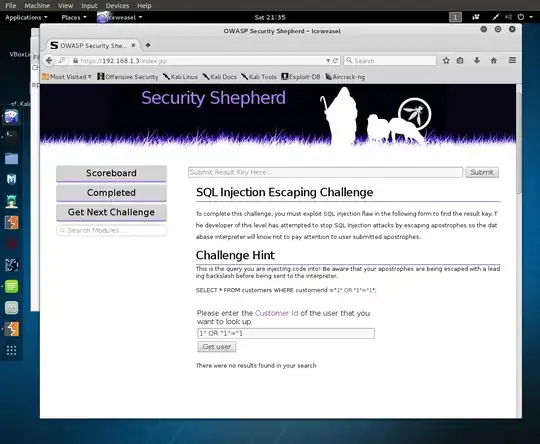
I am using Security Shepherd as a training tool and I am now in the challenge, SQL Injection Escaping Challenge.
The Challenge:
When I make a query just like the one above (just with different table names) in a local database in MySQL it works just fine (I am making the assumption that Shepherd uses MySQL in this challenge since it is the only type of DBMS I have faced until now).
Any idea why the above query might not work as a SQL injection?
The query being used by the backend as mentioned in the hint of the challenge is:
SELECT * FROM customers WHERE customerId="1" OR "1"="1";
The application is escaping any ' by making it \'as a protection against SQL injection. It does not change the ".