The book, Hacking Exposed Industrial Control Systems: ICS and SCADA Security Secrets & Solutions, covers PLC discovery, scanning, modification, intrusion, malware, et al very-well.
For PLCs that connect to TCP/IP-based Modbus or Step7 Communications, in particular, the book mentions many ways to control the PLCs over the network without using the vendor-supplied apps.
For example, with Modbus TCP, one can use modbus-cli to control PLCs including reading or modifying memory (e.g., coils, registers). If you want to discover Modbus TCP devices, you can use the Nmap NSE script, modbus-discover, and to conduct packet-level operations use Wireshark (or tshark) for capture and modbus-vcr for man-in-the middle attacks.
Other tools such as plcscan will discover Modbus TCP and Step7 (s7comm) devices. The s7-info Nmap NSE script will provide more information on the s7comm devices found.
Hacking Exposed Industrial Control Systems also covers Stuxnet in varied depth with links to many other papers such as Symantec's w32-Stuxnet Dossier and the BlackHat 2011 Talk by Dillon Beresford on S7 PLC Exploitation. Here are the basics that the book summarizes:
Stuxnet’s total composition consisted of three modules: one worm and
two payloads. Stuxnet was traditionally introduced into an environment
via a USB flash drive or external hard drive. Immediately on insertion
of the infected media, Stuxnet’s worm capability laterally looked for
any system with Siemens Step7 software running. Stuxnet performed this
search by using techniques such as peer-to-peer RPC
(https://en.wikipedia.org/wiki/Peer-to-peer) to help bypass the
system’s possibility of not being Internet connected. If Step7 was not
found on any laterally connected system, Stuxnet went dormant for a
period of time before rescanning the environment. In the event that
Step7 was identified, a combination of one or both payloads were
executed.
Of the two payloads contained within Stuxnet, one attacked the Siemens
S7-315-2 PLC, which was primarily being used in high-frequency drives
controlling Iranian centrifuges. The other payload, which is less
known, performed a Man-in-The-Middle (MiTM) attack within the PLC. The
payload took any input going to the PLC’s I/O modules and faked them
so any logic within the PLC worked off incorrect logic. The payload
then told the PLC what to do, instead of the PLC listening to the
logic on the system itself. This was the first time any known malware
hid modified PLC code, making Stuxnet the first “PLC rootkit”
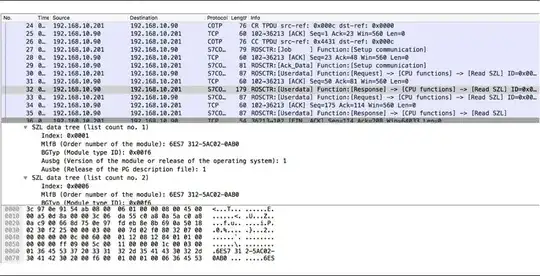
and on Siemens S7comms:
S7comms, or Step 7 communications, is a Siemens protocol implemented
on an ISO protocol that is not open and has very tight controls. For
the 200/300 families of PLCs, you can find some basic information
about the protocol via a Wireshark dissector that is only partially
implemented.
including a packet trace of S7 in action with Wireshark:
The book provides many other resources which I've supplied here along with some others for additional reference --
