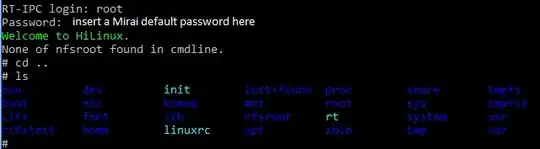
I have dozens of cheap security cameras in my offices. I was under the assumption that, once I changed the admin password, disabled the insecure "P2P Mode", disabled UPNP, disabled guest access and changed default ports I was safe.
After the Mirai hack, I was shocked to see that my "security" camera it's accessible via telnet with root:xc3511.
Now, the telnet port shouldn't be forwarded outside by the router, but still it's a problem. What if some PC on the LAN gets infected by some malware?