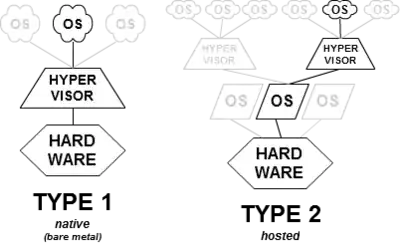
I was looking at a question asking about Dual booting in SuperUser, and I was if there is added protection of using a VM over dual booting. From what I've been told, a VM is it's own sandbox, and that everything that happens (or almost everything) will only affect the VM.
Now, lets say you have 2 HDs, or even 1 HD that is dual booted. Is there the same security sandbox in place at all? I would assume that 2 HDs, would be safer than 1, just in case the Malware is able to spread over the sinlge HD, and could this also might be the same for a VM?
So my questions are.
Is there any security advantages over using a VM vs just dual booting?
Will using the same HD for your Dual Boot/VM cause more security risks due to being on the same HD as your regular boot?
I am assuming that advanced malware, that could attack hardware, would play an issue here, which is why I assume that the same HD could be an issue. Would it be possible for Malware to infect another HD that is a separate boot?
EDIT: It seems that VM is the way to go, which is funny because it seems like a Dual Boot is more work to set up, while being less secure.
To add to another part to the question, are there certain VMs that are much more secure than others, or are they all pretty much the same? One point was saying that some VM use their own kernal, while others will use the Systems, so that seems to be the first step...
But is there anything else we should look for when finding a VM? I know someone who uses VMWare currently, but not sure how good that one is..
Thanks a lot all!