TL;DR: Your phone OS (plus plan provider) can do whatever it wants without your concern, that includes blocking devices it does not want to route the traffic to the open internet. Any traffic through 3G reaches your plan provider 'cause ICC data needs to reach it to allow the connection in the first place. Therefore yes, your mobile operator knows what you're doing.
A phone OS is completely under the control of the vendor (even if you ask about Android, it has proprietary code in the Linux kernel). That gives the vendor complete control over the operation of your device, including all traffic that goes through it. Unless you jailbreak it, and even then you cannot be completely sure if you have complete control. Only full reverse-engineering (of the parts of the OS that are not open source), and a way to modify the memory, will give you full control over the device.
All that said we can get on to the question. When you make a WiFi hotspot or connect a computer through the USB port the device can react (even proprietary embedded OSes use udev these days thanks to GPL tivoization). The reaction of the device can be anything it was programmed to do. Which can really be anything since it can even control kernelmode operation.
Therefore your phone, acting as a router*, can assign markup to the traffic coming through the WiFi hotspot (or USB connection). The markup can be anything: can be as simple as meddling with HTTP headers or more complicated by modifying TCP options. The phone can definitely do this since it has a stateful firewall.
As for identifying yourself as the originator, 3G runs as the 3GPP standard, which is based on GSM, which always adds the ICC data from your SIM card to the connection. Even if your phone does not allow to remove/insert a SIM card, it must have an identifying RFID that can provide an ICC for the 3G connection.
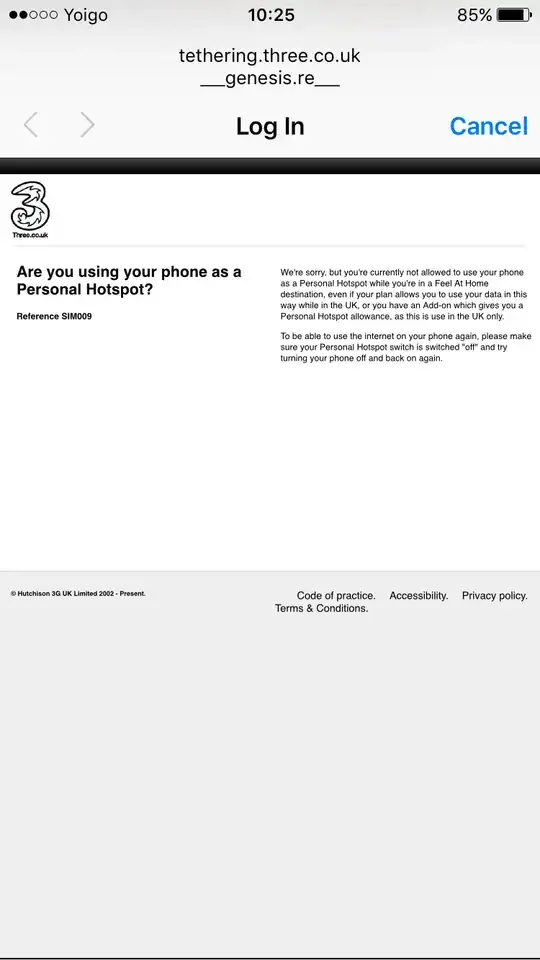
The connection markup is sometimes poorly designed. As in the kindle link you cite, entering the debug mode changed the firewall rules and removed the markup. Sometimes the markup may not be performed by the phone but the receiver of the 3G connection (the company that maintains your plan) may try to identify traffic, possibly as trivially as User-Agent: or in more complex ways (passive fingerprinting).
But there is no way to know how the 3G maintainer performs the filtering (markup on the phone? at kernel level? at firewall level? no markup? user-agent? p0f?) since there are no standards on how to do it and almost all code is proprietary. This is why there are so many ways to jailbreak different phone versions and why this is illegal pretty much anywhere. Reverse engineering the mechanisms how phones perform the not documented features is the Wild West information security today.
One thing you can know is whether the phone is deciding to give you the webpage or it is going all the way to the 3G provider. There are devices that can detect 3G traffic, which may be able to tell you whether the traffic from your machine goes out of the phone or not.
Disclaimer: Again, both jailbreaking and 3G monitoring do have legal implications in several jurisdictions (jailbreaking more than 3G moniotring).
* A phone that can act as a WiFi hotspot or internet connection through USB can be a router since it has two NICs anyway. One NIC through GSM and another through Ethernet over USB or a 802.11 AP