Today, I recieved a message that purports to be from Amazon.
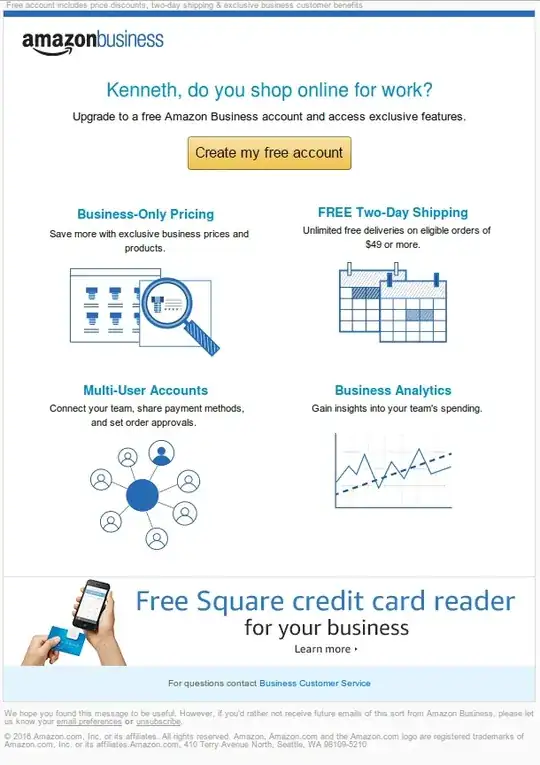 Normally, I can spot a phishing email from a distance. (I work in an ISP's Abuse & NOC department.) But this one seems just slightly off. If it is phishing, it's scary good.
Normally, I can spot a phishing email from a distance. (I work in an ISP's Abuse & NOC department.) But this one seems just slightly off. If it is phishing, it's scary good.
The one hint I have that it's not real is that it was sent to an address of {the A in Q&A}@eoni.com, which doesn't have a Kenneth (it's a tech support address for our ISP that also does domain hosting). The fact that they are using that address makes me think the address could have been automatically collected (whois probably). It is quite possible that one of the domains we host is for a customer named Kenneth, and that that domain has our contact address on the whois record somewhere. We have enough domains hosted that just a first name is not going to be enough to find said domain name and look at the whois record.
Being in the abuse department, I wanted to know if this is real or not (so I can report it if not/possibly block it from working on our network if it is a Phish).
Here's the headers:
Return-Path: <01010157e278aa63-283a615a-b603-4300-8c6f-8426b3978f81-000000@us-west-2.amazonses.com>
Delivered-To: {a in Q&A}@eoni.com
Received: (qmail 8542 invoked from network); 20 Oct 2016 14:22:22 -0000
Received: from a27-163.smtp-out.us-west-2.amazonses.com (HELO a27-163.smtp-out.us-west-2.amazonses.com) (54.240.27.163)
by adam6.eoni.com with (AES128-SHA encrypted) SMTP
(9d6af486-96d0-11e6-bacc-001e67492cec); Thu, 20 Oct 2016 07:22:22 -0700
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/simple;
s=iapqtturmhylirl6i5t3a2ps2ewsadsl; d=business.amazon.com;
t=1476973341;
h=Message-ID:Date:Subject:From:To:MIME-Version:Content-Type:List-Unsubscribe;
bh=CqDwwona4ZmOCsT+zgi3DKmE5lkxklMdpT65fdXrB1c=;
b=UAkSuvsci14jfOFm+fW8S5l3ntdIbESTZB8eHvo6+itz4xiYy9sxXQ1RoXIJIGq9
3ny5HJIKyI6wkjKRWnX6TQ3EHhDqDFlkB75Z1NzHNlp/5NUA8cEa6ua+wq1sWdyG33o
k5gn5Kkz3v72uQMAhT6Dqq/3DSW9ipDMzrHF12Fs=
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/simple;
s=gdwg2y3kokkkj5a55z2ilkup5wp5hhxx; d=amazonses.com; t=1476973341;
h=Message-ID:Date:Subject:From:To:MIME-Version:Content-Type:List-Unsubscribe:Feedback-ID;
bh=CqDwwona4ZmOCsT+zgi3DKmE5lkxklMdpT65fdXrB1c=;
b=BdhqUbp6t3dhXe83M3isFcjV2hXaT6rAhCxPN/WXWepJngjhi1EO3Sgd5SbkaEjj
6dzzlfljD+nKTJH2r9Kd1COeXqc5tgSeMEmVYV1TpmIRhc1fU9RUULRKG4ojxs0msSb
RDRzSCa83Se484s7KDNwb5LWixFn7jo3oL7DFKx0=
Message-ID: <01010157e278aa63-283a615a-b603-4300-8c6f-8426b3978f81-000000@us-west-2.amazonses.com>
Date: Thu, 20 Oct 2016 14:22:21 +0000
Subject: Free Upgrade to Amazon Business Account
From: Amazon <no-reply@business.amazon.com>
To: {A in Q&A}@eoni.com
MIME-Version: 1.0
Content-Type: multipart/alternative;
boundary="_=_swift_v4_1476973341_6e5cebc34b840a2a68132f6e212fdc76_=_"
X-Pardot-Route: 113:54552:359489270
List-Unsubscribe: <http://www.amazonbusiness.com/unsubscribe/u/54552/6674f6c0dd8377b4a26688a664718cffd707396fd788791d186acab4a81bd210/359489270>
X-Report-Abuse-To: abuse@pd25.com
X-SES-Outgoing: 2016.10.20-54.240.27.163
Feedback-ID: 1.us-west-2.DslCQSzKRwSQ0bYxCfi+GcY39H31l7QrR+kFUIOTrc4=:AmazonSES
X-MagicMail-OS: Inactive
X-MagicMail-UUID: 9d6af486-96d0-11e6-bacc-001e67492cec
X-MagicMail-SourceIP: 54.240.27.163
X-MagicMail-RegexMatch: 0
X-MagicMail-EnvelopeFrom: <01010157e278aa63-283a615a-b603-4300-8c6f-8426b3978f81-000000@us-west-2.amazonses.com>
X-MagicMail-Original-Destination: {A in Q&A}@eoni.com
X-MagicMail-Quarantine: Yes
Looking at the headers, I see it is from what I believe is an AWS email service. (Anyone can buy that and send email). So that doesn't convince me it's Amazon. I see stuff about about Pardot, a salesforce B2B Marketing automation system. That seems odd that it wouldn't be in house to Amazon, but they could use a system like that. So not sure what to think on that.
If this is an attack, it has to work somehow. Where do the links go?
Create my account: http:/www.amazonbusiness.com/e/54552/gistration-start-ref-b2b-e459b/jt2hvr/359489270
Unsubscribe: http:/www.amazonbusiness.com/preferences/?ehash=6674f6c0dd8377b4a26688a664718cffd707396fd788791d186acab4a81bd210&email_id=359489270
Update email preferences: http:/www.amazonbusiness.com/preferences/?ehash=6674f6c0dd8377b4a26688a664718cffd707396fd788791d186acab4a81bd210&email_id=359489270
None of these have SSL, but the Create my account one redirects to:
https:/www.amazon.com/ap/signin?openid.return_to=https%3A%2F%2Fwww.amazon.com%2Fbb%2Fregistration%2Fconfirmation%2Fref%3Db2b_reg_st_rd&openid.identity=http%3A%2F%2Fspecs.openid.net%2Fauth%2F2.0%2Fidentifier_select&openid.assoc_handle=usflex&openid.mode=checkid_setup&marketPlaceId=ATVPDKIKX0DER&openid.claimed_id=http%3A%2F%2Fspecs.openid.net%2Fauth%2F2.0%2Fidentifier_select&pageId=authportal_b2b_login&openid.ns=http%3A%2F%2Fspecs.openid.net%2Fauth%2F2.0&openid.pape.max_auth_age=0&siteState=pageFlowType%3DLOGIN%2CclientContext%3D168-4326428-9305323%2CsourceUrl%3Dhttps%253A%252F%252Fwww.amazon.com%252Fbb%252Fregistration%252Fconfirmation%252Fref%253Db2b_reg_st_rd%2Csignature%3DLXjj2FO0jmvxdiEVn0vZfa3j2BZbIE4j3D&ref_=null
Ok, where is this amazonbusiness.com domain hosted? Who owns the name? Surely Amazon would host all of their sites on AWS, right?
dig a www.amazonbusiness.com
; <<>> DiG 9.10.3-P4-Ubuntu <<>> a www.amazonbusiness.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58074
;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;www.amazonbusiness.com. IN A
;; ANSWER SECTION:
www.amazonbusiness.com. 820 IN CNAME go.pardot.com.
go.pardot.com. 7199 IN CNAME pi.pardot.com.
pi.pardot.com. 29 IN CNAME pi-dfw.pardot.com.
pi-dfw.pardot.com. 29 IN CNAME pi-dfw-lb1.pardot.com.
pi-dfw-lb1.pardot.com. 899 IN A 136.147.104.32
;; Query time: 57 msec
;; SERVER: 192.168.88.1#53(192.168.88.1)
;; WHEN: Thu Oct 20 08:21:50 PDT 2016
;; MSG SIZE rcvd: 143
Compare that to amazon.com itself:
dig a amazon.com
; <<>> DiG 9.10.3-P4-Ubuntu <<>> a amazon.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 40326
;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;amazon.com. IN A
;; ANSWER SECTION:
amazon.com. 23 IN A 54.239.25.208
amazon.com. 23 IN A 54.239.17.7
amazon.com. 23 IN A 54.239.26.128
amazon.com. 23 IN A 54.239.25.192
amazon.com. 23 IN A 54.239.17.6
amazon.com. 23 IN A 54.239.25.200
;; Query time: 1 msec
;; SERVER: 192.168.88.1#53(192.168.88.1)
;; WHEN: Thu Oct 20 09:02:34 PDT 2016
;; MSG SIZE rcvd: 124
Ok, so who owns the IP address space for the possibly fake site:
whois 136.147.104.32
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/public/whoisinaccuracy/index.xhtml
#
#
# The following results may also be obtained via:
# https://whois.arin.net/rest/nets;q=136.147.104.32?showDetails=true&showARIN=false&showNonArinTopLevelNet=false&ext=netref2
#
NetRange: 136.147.0.0 - 136.147.255.255
CIDR: 136.147.0.0/16
NetName: SFDC-3
NetHandle: NET-136-147-0-0-1
Parent: NET136 (NET-136-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS14340
Organization: Salesforce.com, Inc. (SALESF-3)
RegDate: 2012-02-24
Updated: 2014-07-14
Ref: https://whois.arin.net/rest/net/NET-136-147-0-0-1
OrgName: Salesforce.com, Inc.
OrgId: SALESF-3
Address: 1 Market Street
Address: Suite 300
City: San Francisco
StateProv: CA
PostalCode: 94105
Country: US
RegDate: 1999-11-30
Updated: 2014-11-20
Ref: https://whois.arin.net/rest/org/SALESF-3
OrgAbuseHandle: NOC1403-ARIN
OrgAbuseName: Network Operations Center
OrgAbusePhone: +1-415-901-7000
OrgAbuseEmail: arin@salesforce.com
OrgAbuseRef: https://whois.arin.net/rest/poc/NOC1403-ARIN
OrgNOCHandle: NOC1403-ARIN
OrgNOCName: Network Operations Center
OrgNOCPhone: +1-415-901-7000
OrgNOCEmail: arin@salesforce.com
OrgNOCRef: https://whois.arin.net/rest/poc/NOC1403-ARIN
OrgAbuseHandle: SAN76-ARIN
OrgAbuseName: Salesforce Abuse NOC
OrgAbusePhone: +1-703-463-3219
OrgAbuseEmail: abuse@salesforce.com
OrgAbuseRef: https://whois.arin.net/rest/poc/SAN76-ARIN
OrgTechHandle: NOC1403-ARIN
OrgTechName: Network Operations Center
OrgTechPhone: +1-415-901-7000
OrgTechEmail: arin@salesforce.com
OrgTechRef: https://whois.arin.net/rest/poc/NOC1403-ARIN
RNOCHandle: NOC1403-ARIN
RNOCName: Network Operations Center
RNOCPhone: +1-415-901-7000
RNOCEmail: arin@salesforce.com
RNOCRef: https://whois.arin.net/rest/poc/NOC1403-ARIN
RAbuseHandle: SAN76-ARIN
RAbuseName: Salesforce Abuse NOC
RAbusePhone: +1-703-463-3219
RAbuseEmail: abuse@salesforce.com
RAbuseRef: https://whois.arin.net/rest/poc/SAN76-ARIN
RTechHandle: NOC1403-ARIN
RTechName: Network Operations Center
RTechPhone: +1-415-901-7000
RTechEmail: arin@salesforce.com
RTechRef: https://whois.arin.net/rest/poc/NOC1403-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/public/whoisinaccuracy/index.xhtml
#
So NOT on AWS. Compare to who owns the IP address space hosting Amazon.com:
whois 54.239.26.128
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/public/whoisinaccuracy/index.xhtml
#
#
# The following results may also be obtained via:
# https://whois.arin.net/rest/nets;q=54.239.26.128?showDetails=true&showARIN=false&showNonArinTopLevelNet=false&ext=netref2
#
NetRange: 54.224.0.0 - 54.239.255.255
CIDR: 54.224.0.0/12
NetName: AMAZON-2011L
NetHandle: NET-54-224-0-0-1
Parent: NET54 (NET-54-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS16509
Organization: Amazon Technologies Inc. (AT-88-Z)
RegDate: 2012-03-01
Updated: 2012-04-02
Ref: https://whois.arin.net/rest/net/NET-54-224-0-0-1
OrgName: Amazon Technologies Inc.
OrgId: AT-88-Z
Address: 410 Terry Ave N.
City: Seattle
StateProv: WA
PostalCode: 98109
Country: US
RegDate: 2011-12-08
Updated: 2014-10-20
Comment: All abuse reports MUST include:
Comment: * src IP
Comment: * dest IP (your IP)
Comment: * dest port
Comment: * Accurate date/timestamp and timezone of activity
Comment: * Intensity/frequency (short log extracts)
Comment: * Your contact details (phone and email) Without these we will be unable to identify the correct owner of the IP address at that point in time.
Ref: https://whois.arin.net/rest/org/AT-88-Z
OrgTechHandle: ANO24-ARIN
OrgTechName: Amazon EC2 Network Operations
OrgTechPhone: +1-206-266-4064
OrgTechEmail: amzn-noc-contact@amazon.com
OrgTechRef: https://whois.arin.net/rest/poc/ANO24-ARIN
OrgAbuseHandle: AEA8-ARIN
OrgAbuseName: Amazon EC2 Abuse
OrgAbusePhone: +1-206-266-4064
OrgAbuseEmail: abuse@amazonaws.com
OrgAbuseRef: https://whois.arin.net/rest/poc/AEA8-ARIN
OrgNOCHandle: AANO1-ARIN
OrgNOCName: Amazon AWS Network Operations
OrgNOCPhone: +1-206-266-4064
OrgNOCEmail: amzn-noc-contact@amazon.com
OrgNOCRef: https://whois.arin.net/rest/poc/AANO1-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/public/whoisinaccuracy/index.xhtml
#
So Amazon.com is on AWS, just like I thought it would be.
At this point, I'm not sure whether the email is fake or not. Is it? If so, how does it work? It seems to be doing something with OpenID, what's going on there? How could I know for sure in the future?