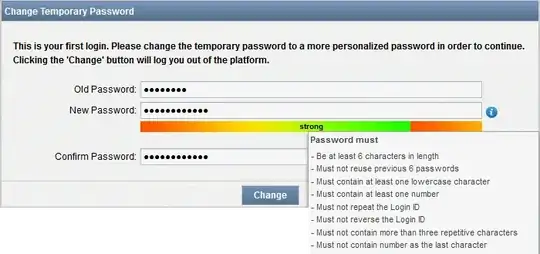
In configuring a new system today (Juniper Space, Linux-based Network Management platform), I came across a bizarre password requirement that I'm curious about. Upon logging into the web UI with the default credentials, I was prompted to change the password, which is good, and I went to do, but my randomly generated password was rejected because the last character was a number. This struck me as all the more strange, given that the password I provided for the command line interface ended in a number, and it was accepted.
In my experience, password requirements like this generally have some underlying reasoning behind them, like Q and Z not being present on old telephone keypads, or legacy systems compatibility or just plain poor systems/policies/whatever. I'm having a much more difficult time explaining this particular policy with any of those explanations, though.
Does anyone have any insight into the reasoning behind a password policy that would prohibit a numeric last character?