I recently started to use grafana to visualize a lot of different metrics. Grafana also enables me to share dashboard snapshots directly via a link. Which is pretty comfortable since I can share the dashboard without the need for others to be registered at my site. Such a link would look like the following:
https://my-website.com:3000/dashboard/snapshot/2yFejTCJX4G8Q4Ea2XiCpMhQuiUTDvyu
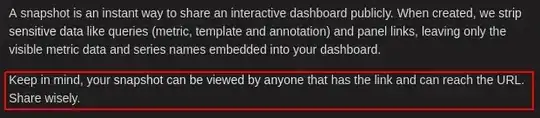
In the process of creating such a link grafana warns me about the following:
Its clear to me that for the case I send the link to person A, I can never say to whom he will send that link too.
But if we consider a scenario where the dashboard snapshot shows data which is related to person A. Person A obviously don't want that random strangers can access his information.
1) Is it a bad idea now if I create the link and send it to person A with the warning he should not share it with others since every one with the link can access his dashboard?
2)Is this approach more risky than the normal login way? Since with the normal login approach there is also the risk person A shares his login/password with others?
3) Is it generally possible to get access to all of the dasboard snapshots with some kind of brute force attack ?
Link to the documentation about dashboard sharing: Link