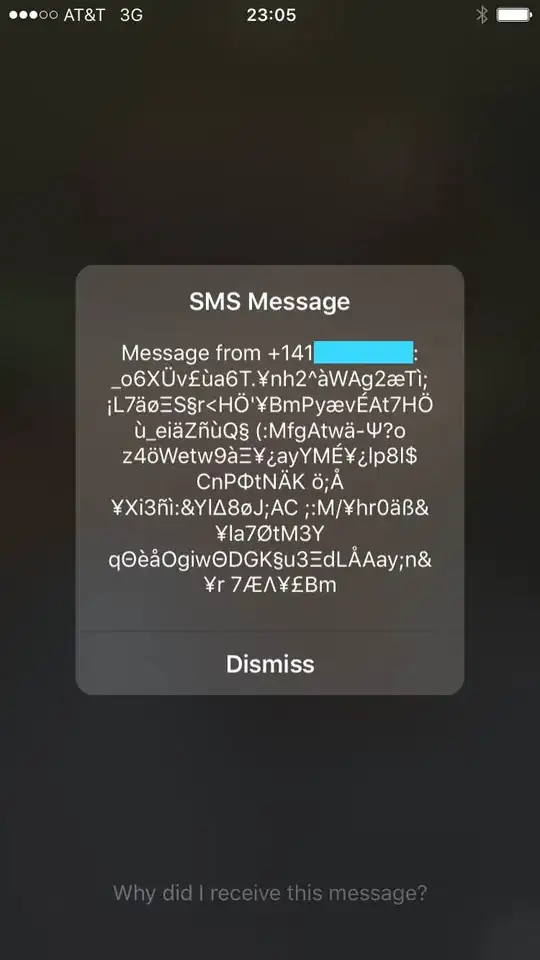
On device tests
Check the logs off the previous batches of texts; if they came in some what regular intervals and then stopped I'd take that as a sign of automated hacking attempts. And their stopping as a sign that either; they ran out of exploits to try, or had one succeed in pwnage.
Check the time stamp of latest system update, if messages resumed shortly after an upgrade then I'd take that as a sign that it was once in a bot-net and is being re-assimilated once again.
Suggested actions
Do not respond to the number. Some automated phishing/malware deployment scripts seem to be testing for text compatibility before attempting to send payloads.
Do not plug the device into any computer; not even for forensics! I've already heard one horror story that didn't end well when an infected phone touched a PC in a USB way.
Do not allow it on your local Wi-Fi network. While I've not seen malware jump over Wi-Fi in the wild (between phones and PC that is) I've tested if possible on Android and it isn't hard.. on my own devices only (I'm not a distributor) which you can read up on it at Stack Overflow where I've detailed how to get Android running Metasploit.
Do take the device into the dealer and make them explain what those messages are. If they can't figure it out ask for their security department contact details.
Do contact the security department for the devices service provider. Ask them to either monitor the account and traffic for suspicious activity or send them the device for imaging. Their hardware is put at risk instead of you own.
Check the local laws regarding harassment. If the texts are coming in at times that are legally defined as an inconvenience then you maybe able to take this issue to government agencies responsible for enforcement and investigation.
I've experienced having to report possible security issues to two different service providers and can say that you'll need to be patient & persistent. This is because from my expenses to get in contact with both the right department and the correct person took multiple calls, transfers, and luck. Most will tell you to turn it off and back on again in which case ask to be transferred up the chain till you get someone with more that the minimum required metal capabilities to be considered living and warm.
That all being said the best course of action is to notify the service provider because not notifying them may make you partly liable for damages done to other servers or devices. Think of it like knowingly spreading an infectious disease if you don't notify them because that device is showing symptoms.
Edits & updates
Additional malware hunting options
Both Android and iPhone have an interesting bug/feature involving Airplane mode which I documented a bit at Security Stack Exchange here's the relevant quote...
For Rooted Android (attacking/sniffing) I like InterceterNG and DSploit for intercepting traffic between another device and it's WiFi access point. However for this to work on cell phones and force all traffic through the WiFi the target should first be put into 'Airplane Mode' and then have it's WiFi turned on. Then fire up interceptor on the attacking Android device and sniff away. WireSkark helps with pcap files but if you just need IPs and packets with time stamp IntercepterNG is great on the go; it'll even try to help strip https.
... the suggested course of action was to intentionally "Man in The Middle" (MiTM) attack the device's Wi-Fi and profile it's traffic.
Note this trick with airplane mode also works for Bluetooth sniffing.