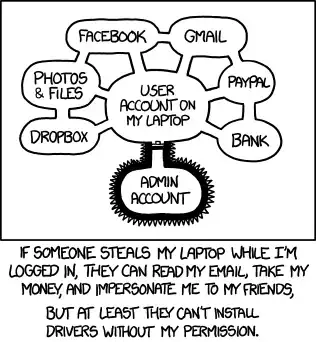
Separating privileges, i.e using a non-admin account and escalating only when needed, seems to be something everyone agrees on. I can roughly understand why it's important on every system : prevent an attacker from modifying the system and taking complete control of the machine, and on shared systems, prevent a user's mistake from propagating to the others.
However, on a personal computer, all the data I care about is in my user folder, which is accessible without admin rights by every program running on the computer. Basically, if a malware runs, I've lost, be it with admin rights or not. All the damage can be done without admin rights, and reinstalling the system to nuke the malware is easy.
In this context, why is using a non-admin account so important ?
Please keep in mind that I already know some of the reasons and am not advocating going back to XP's default policy. I just want to know if there are some reasons I missed.
Relevant xkcd :