[ THIS POST IS OBSOLETE. FOR HISTORICAL PURPOSES ONLY AS EXAMPLE OF THE DIFFICULTY GETTING EARLY VERSIONS OF VC TO RUN]
2On an InsydeH20 V5.0 UEFI "BIOS" running on Acer E5-575:
Install all latest Win10 updates
Boot to UEFI, press F2 on Acer machines at 2x sec during boot
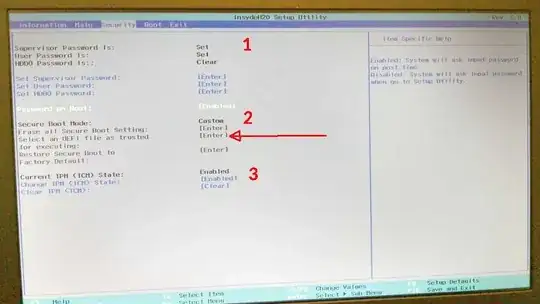
Turn secure boot off [ A on pics] set it as 'disabled'
IMPORTANT in UEFI: set System Admin and user passwords [1 on pics], and set Password on boot option. Do not set hard disk password as it may interfere with Win10 updates. Admin and user password on UEFI will stop all Win10 reboots at UEFI/BIOS interface so you can interrupt auto-boots to troubleshoot Veracrypt faster, and stop direct writes to UEFI by malware
Run Veracrypt 1.19 disk partition encryption
If it fails one pass, do it again. It should pass the 2nd + attempt. If not boot via rescue disk. This is because UEFI doesn't recognize the location or the file itself "veracryptb", the bootloader, in the hard disk as "trusted."
If Veracrypt fails still: STOP, and proceed only if you know UEFI, Veracrypt and Win10 well as written below.
* If Veracrypt fails still, but boots on rescue disk proceed with caution as noted above. *
Complete Veracrypt full disk encryption
Once completed, and reboots, enter UEFI/BIOS
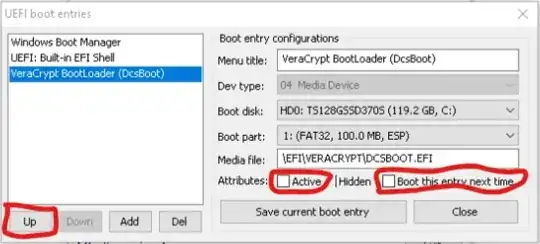
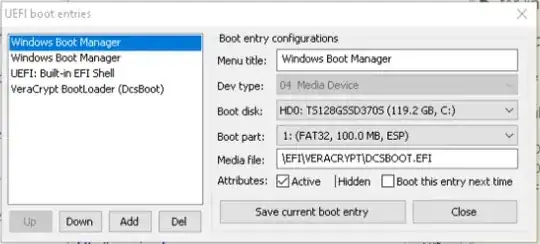
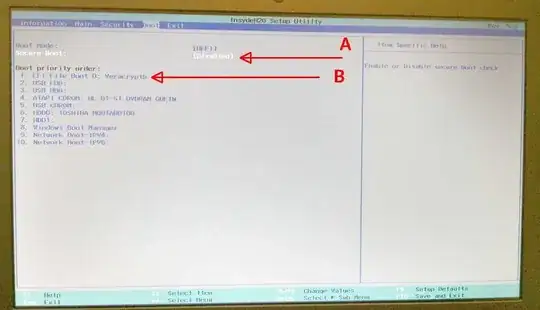
Turn ON secure boot [ A on pic], it allows edits to boot files list to mark
them 'trusted' [2 on pic]
Edit secure boot file list
On the boot order screen, locate veracrypt and move it to the top of the
boot priority order. Move Windows Boot Manager to near bottom [B on pic].
Turn Secure Boot off, the Veracrypt bootloader will remain at the
top and the list of bootloaders is now not editable
Reboot
Enjoy.
NB: Secure boot must be off permanently because the Veracrypt signature does not reside in a separate UEFI secure boot table in firmware. You can generate one and enter it, as described in the Veracrypt forum or run without secure boot. I suggest leave SECURE BOOT OFF as the Veracrypt signature generating script has bricked some UEFI/BIOS. A malware bootloader cannot run in the UEFI because to boot, it must be added to trusted list which can be done only with SECURE BOOT ON to edit the boot file trusted list; malware cannot do that without the UEFI Admin password to change the UEFI settings from SECURE BOOT OFF. So far, rootkit malware cannot run below or at the UEFI preboot level, as we know today, to hack the admin password in UEFI, so it remains secure even with SECURE BOOT OFF. With SECURE BOOT ON, if the malware signature adds itself to the trust list it still does not exist in SECURE BOOT table in firmware so cannot run. However, Veracrypt has a script to add its signature to the firmware trust table [ with mixed results] so its possible for malware to do the same with SECURE BOOT ON. Malware may boot if its tries to mimic the trusted files in UEFI InsydeH20 table with SECURE BOOT OFF if InsydeH20 doesn't use signatures to secure its integrity. The prior post shows another user renamed veracryptb to Windows Boot Manager and booted, showing mimic ploy can work for the Windows Boot Manager. However its not easy to mimic the veracryptb bootloader due to the keys generated during the creation of the secure partition that is unique to each bootloader, a mimic will likely fail to boot into veracrypt. The above applies only to the INsydeH20 UEFI implementation, for your UEFI, YMMV.
Do not edit the TPM state unless you are sure. If the signatures cannot be generated on-the-fly or are factory supplied only, clearing the state may brick the PC [ 3 on pic].