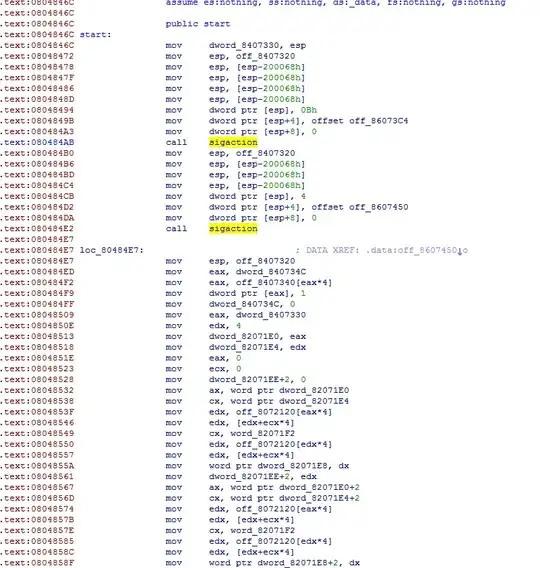
I have a binary file which uses some exploit(i guess, it was generated with metasploit), but I can`t determine the exact exploit it uses.
The disassembly listing of it contains a plenty of "mov" operators, and .data section contains a lot of strings like:
"!!\"#$$%&''()**+,--./0112344567789::;<==>?@@ABCCDEFFGHIIJKLLMNOOPQRRSTUUVWXXYZ[[\]^^_`abbcdeefghhijkklmnnopqqrsttuvwwxyzz{|}}~"
And assembler code consists of plenty "mov"s
Is there any way to define which exploit this malicious binary uses?