When I run an anti-virus scan (Kaspersky in this case) on an (InnoSetup) installer, it scans multiple "data" objects which seem to be the files within the installer:
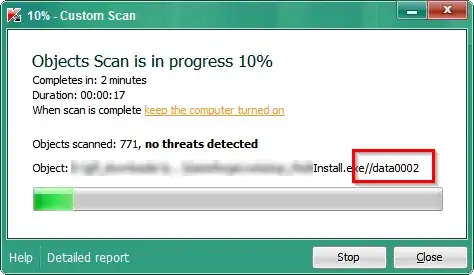
This gives the impression that it would detect a malicious program even before running the installer.
Can I rely on the anti-virus software detecting a malicious program within an installer when scanning just the installer?
Even if the installer is password protected and encrypted?
Or do I need to scan the installed files as well?
Note: I know that it is dangerous to run an installer from an untrusted source. In my special scenario, the installer itself is created by a trusted source but the contents are not necessarily trusted.