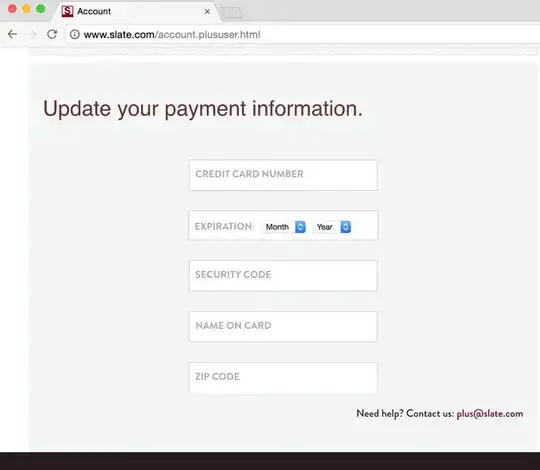
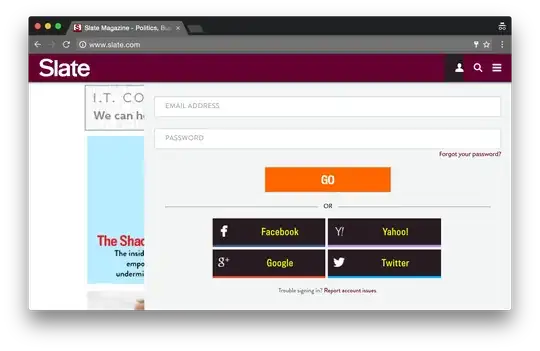
Caveat, IANAQSA
Update: Slate isn't actually a SAQ A - they aren't using iframes, and they're submitting card info to, for example, https://profile.slate.com/widget/traditional_register.jsonp... most of what's below still applies in spirit though.
Could someone tell me if it is possible to securely get credit card information in the way they have described?
Yes, it is possible. However, there is some implied responsibility shifted to you to check that your connection is secure and that the payment site you go to is a legitimate payment processor.
That said, this configuration is both acceptable (as per PCI) and mildly inadvisable (per security best practices).
A reading of SAQ A - which applies to merchants who outsource all card handling to their processor via an iframe - suggests that this is a legal configuration. Note that it does not place any explicit requirements on the pages containing the payment page (iframe) enclosing the Service Provider's payment page(s); just the SP's page(s) come from the SP and the SP is PCI DSS compliant (which implies encryption):
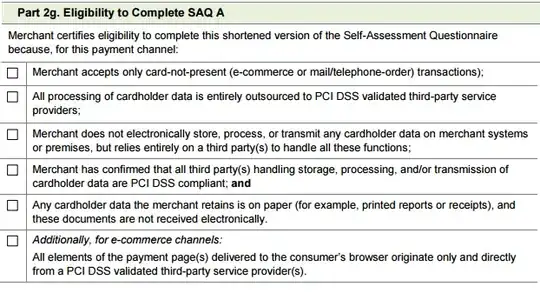
Now, that being said, there are issues such as MITM that make the lack of outer encryption by Slate inadvisable. Many organizations have fought their way over this hump and eventually decided that encrypting everything on their site was preferable to dealing with the perception of insecurity. But it usually takes time and complaints before they organizations get there. So feel free to complain about this.