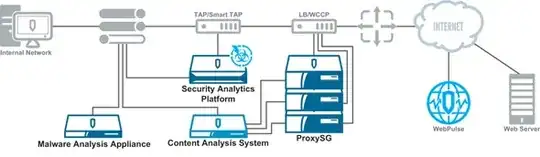
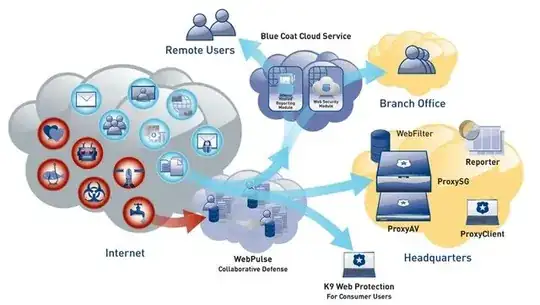
The BlueCoat Unified Agent has been built to provide security on the cloud. The Unified Agent client monitors the Internet Breakout IP being used by the user and switches from Active to Passive mode or vice versa depending on the company policy.
For example a company might have on-premise proxy servers. Therefore when the client uses the laptop inside the company network perimeter, the client falls into passive mode and lets the on-premise proxy servers handle the "washing" of the Internet traffic.
However if the client goes at home, or a hotel or any other place with a public Internet breakout IP which is not defined as a Corporate Internet IP by that company, the client will immediately switch to 'Active' state. That means that the client establishes an encrypted IPSec tunnel towards the nearest BlueCoat ThreatPulse data center and a proxy cloud server does all the security traffic "checking" on the cloud. Companies can sync their on-prem proxies to have the exact policy on the cloud but that is optional.
Additionally, companies that use the Unificed Agent can also define subnets / IP Addresses / URLs which are like an exception for the unified agent and that traffic goes direct to the destination without utilizing the IPSec tunnel (Split Tunnelling). The above environment is also known as Hybrid (utilizes both on-prem and cloud proxies)
Moreover you can have a pure cloud environment. A lot of companies do not have on-premise proxies and they use the Unified Agent both inside and outside the Company Network perimeter.All those are possible setups of the Unified Agent (plus many more of course).
The key advantage of the Unified Agent is that it provides extra security layers. When a client makes a request, it will go to the Cloud Proxy, the proxy will check if the content should be obtained based on the company URL policy (i.e. the company could be blocking porn, etc.). If it is OK, it will obtain the content and AV scan it using AV engines on the cloud from 3rd party vendors like Kaspersky, TrendMicro, Symantec etc. It will also optionally send the obtained data to a sandboxing environment if the file signatures are unknown. If everything is OK, it will deliver the content to the end-point client.
Back to your question, a lot could cause crashing of the actual application. In any case you should check with IT support of your company. You can also check the Windows logs as it will have application logs for the Unified Agent. Also the Unified Agent offers a "tracing" functionality if the crashing happens while you are visiting specific URLs, etc.