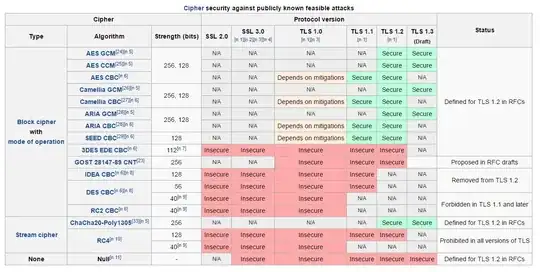
I need to disable the weak ciphers within a weak protocol version, namely TLS1.0, on a windows server 2012 R2 running IIS. I understand that cipher suites are tied to protocol, i.e. TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 would be specific to TLS. I am able to disable the cipher suite in regedit, but I am unable to do so only for TLS version 1.0.
Context
Part of my hardening of IIS8.5 requires the disabling of TLS1.0, which unfortunately I cannot do so due to business requirements (client machines that I do not have control over do not have TLS1.2 enabled). The next best alternative would be to disable the as many ciphers for TLS1.0 that business don't require.
Can anyone shed some light?