Yes it does, but you have to take into consideration the probability of collision not only size of key space.
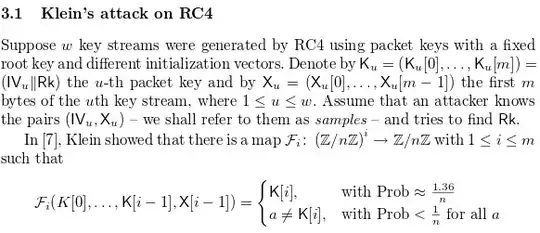
As you said the key space for WEP is 224, with this key space there is a 50% collision after only 212 packets, so you don't actually need to go over the 224 packets to find a collision. After only 12430 frames you get 99% collision probability, so from there you can see that 224 key space is a really low number in order to secure WEP.
To go through the math you'll need to check out the Birthday attack which is uses the birthday paradox probabilistic model to reduce the complexity of finding a collision. It's actually pretty interesting to have a look at (it's also used in order to compute MD5 collisions). Basically it's based in the probability of finding 2 people that have the birthday in the same day in a set of N people randomly chosen.
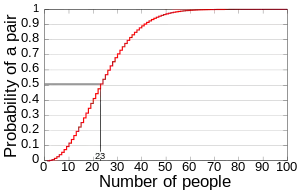
As you can see probability reaches 100% with 367 persons since there are 366 possible birthdays but with only 23 people you get 50% chance of collision!
The problem is that WEP uses RC4 which is a steam cipher, that means that no cipher key can be reused. This would mean that BSS would need to change its cipher key as soon as all 224 keys have been consumed, but WEP protocol doesn't implement something like this.
WEP uses the same base key for all users so the security of WEP is based on never recycling a pair of [Base_Key,IV].
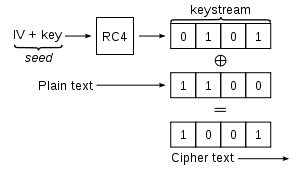
For the given scheme WEP would need an avoidance algorithm to avoid to different nodes to reuse the same IV, but again WEP doesn't implement something like this.
What WEP does is randomly selecting an IV from the 224 key space, and this is where the Birthday paradox comes into play.