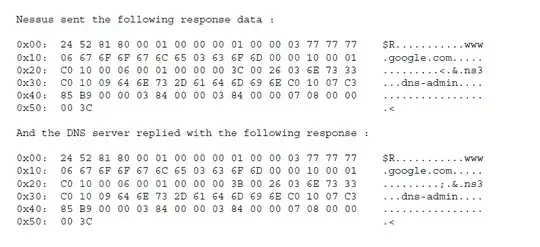
I use Nessus to check vulnerabilities on my webserver. It is a Windows Server. Nessus reports that this particular server has a CVE-2004-0789 vulnerability.
Here is the description from Nessus:
The remote DNS server is vulnerable to a denial of service attack because it replies to DNS responses.
An attacker could exploit this vulnerability by spoofing a DNS packet so that it appears to come from 127.0.0.1 and
make the remote DNS server enter into an infinite loop, therefore denying service to legitimate users.
How to check if this vulnerability really exists on my server? Is there any proof of concept about this?
[UPDATE: Some screenshot from Nessus' report]