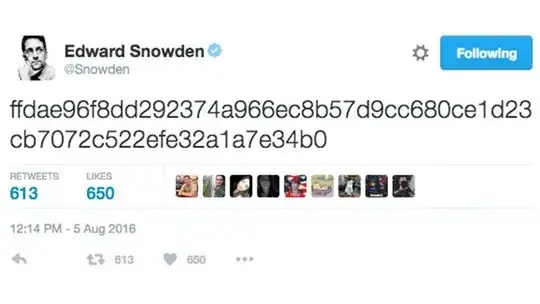
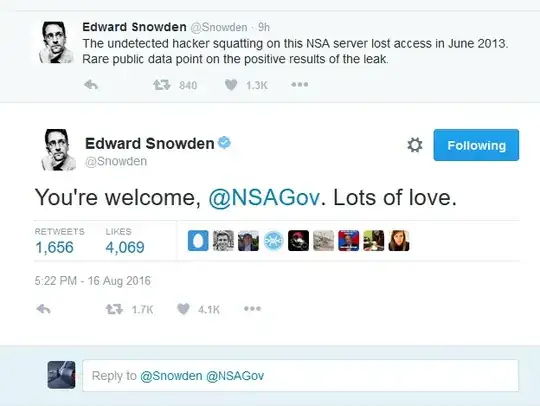
First Hand Details: TEG (The Equation Group) is NSA's team of hackers who'd write code to exploit systems worldwide. Some of the private files were recently dropped by a group called Shadow Brokers & they've auctioned it in exchange for BTC bids .. I could trail back to the below mentioned keys which were earlier released previous week by Snowden (if anyhow it's linked {it's just sitting here for references}):
Probable Agenda: As taken inputs from @atdre answer to explain the agenda - there are different versions of the primary agenda as below:
http://www.businessinsider.in/A-shadowy-group-claims-to-have-hacked-an-elite-hacking-group-linked-to-the-NSA/articleshow/53712768.cms
Sources:
- Wikileaks Intention to release the same files
- RT's version of Cyber Weapon Disclosures
- Sputnik's version of Malware Scandal by NSA
- Analysis suggests revisions of malware & resemblance to older versions
- Shadowbrokers Tainted Bitcoin Transactions, US Involved!? A Question.
- Shadowbrokers drops IP Ranges NSA Targeted
- Shadowbrokers exits the scene
- ShadowBrokers Exploit(s) Released
Official Sources Timeline:
- The first official after Wikileaks probability of intent to disclose the same set of files, Edward Snowden comes up with a teensy bit of a diplomatic pressure statement. Thanks to @WhiteWinterWolf to report this one out.
Some Analysis of the released files Reported:
- Analysis by Risk Based Security over The Equation's Group Files
- Analysis by Matt Suiche, MVP - Microsoft via Medium
- BENIGNCERTAIN Analysis confirmed by The Intercept
Solved Proof Of Concept & it's Working State:
- XORCat's EXBE (ExtraBacon) POC from TEG file: The exploits appear to be targeting firewalls, particularly Cisco PIX/ASA, Juniper Netscreen, Fortigate, and more as per analyst.
Questions: The Equation Group were hacked (NSA) & it's a wonder if they aren't backdoor!? Of-course we go through the code .. but could anyone let us know if these files are genuine?
Also, what's the use of the files, what they specifically target? These files landed originally at:
https://theshadowbrokers.tumblr.com
Now they are gone, the links they've provided are gone (except one which's here) & the original copies might have been already backdoored (later ones which might pop up). I read it's related to Stuxnet (or more powerful, I know that Stuxnet targeted Nuclear Facilities) but now that they are gone .. can anyone let know the real intent of the files & the groups they've mentioned as inline:
What does each of the section specifically does? All inputs are appreciated & links to this one to be updated one by one as the reason becomes clear.
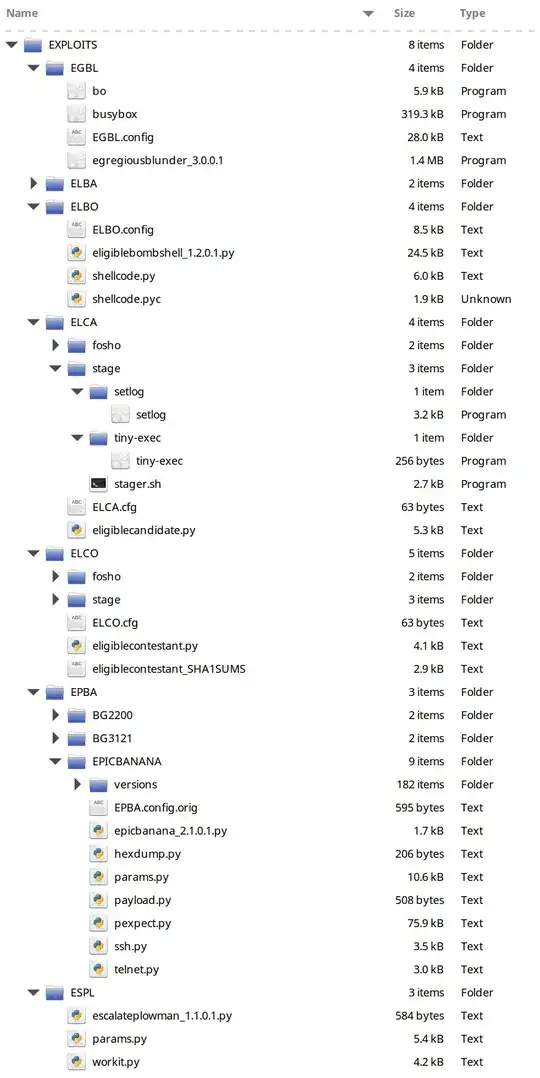
EDIT: As of Apr, 2017 - Shadown Brokers have released the exploit packages, here are some samples which are on the release:
Exploits
EARLYSHOVEL RedHat 7.0 - 7.1 Sendmail 8.11.x exploit
EBBISLAND (EBBSHAVE) root RCE via RPC XDR overflow in Solaris 6, 7, 8, 9 & 10 (possibly newer) both SPARC and x86.
ECHOWRECKER remote Samba 3.0.x Linux exploit.
EASYBEE appears to be an MDaemon email server vulnerability
EASYPI is an IBM Lotus Notes exploit that gets detected as Stuxnet
EWOKFRENZY is an exploit for IBM Lotus Domino 6.5.4 & 7.0.2
EXPLODINGCAN is an IIS 6.0 exploit that creates a remote backdoor
ETERNALROMANCE is a SMB1 exploit over TCP port 445 which targets XP, 2003, Vista, 7, Windows 8, 2008, 2008 R2, and gives SYSTEM privileges (MS17-010)
EDUCATEDSCHOLAR is a SMB exploit (MS09-050)
EMERALDTHREAD is a SMB exploit for Windows XP and Server 2003 (MS10-061)
EMPHASISMINE is a remote IMAP exploit for IBM Lotus Domino 6.6.4 to 8.5.2
ENGLISHMANSDENTIST sets Outlook Exchange WebAccess rules to trigger executable code on the client's side to send an email to other users
EPICHERO 0-day exploit (RCE) for Avaya Call Server
ERRATICGOPHER is a SMBv1 exploit targeting Windows XP and Server 2003
ETERNALSYNERGY is a SMBv3 remote code execution flaw for Windows 8 and Server 2012 SP0 (MS17-010)
ETERNALBLUE is a SMBv2 exploit for Windows 7 SP1 (MS17-010)
ETERNALCHAMPION is a SMBv1 exploit
ESKIMOROLL is a Kerberos exploit targeting 2000, 2003, 2008 and 2008 R2 domain controllers
ESTEEMAUDIT is an RDP exploit and backdoor for Windows Server 2003
ECLIPSEDWING is an RCE exploit for the Server service in Windows Server 2008 and later (MS08-067)
ETRE is an exploit for IMail 8.10 to 8.22
FUZZBUNCH is an exploit framework, similar to MetaSploit
ODDJOB is an implant builder and C&C server that can deliver exploits for Windows 2000 and later, also not detected by any AV vendors
Utilities
PASSFREELY utility which "Bypasses authentication for Oracle servers"
SMBTOUCH check if the target is vulnerable to samba exploits like ETERNALSYNERGY, ETERNALBLUE, ETERNALROMANCE
ERRATICGOPHERTOUCH Check if the target is running some RPC
IISTOUCH check if the running IIS version is vulnerable
RPCOUTCH get info about windows via RPC
DOPU used to connect to machines exploited by ETERNALCHAMPIONS
GitHub Reference: https://github.com/misterch0c/shadowbroker