Is it possible [for the BBC organisation] to detect packet content of encrypted wi-fi transmissions?
The answer that question has to really be: who knows what secret capabilities they have?
But in regard to the question of
can the BBC tell if I am using iPlayer?
In my opinion, yes definitely.
The reconciliation of your geo-location (obtained via your wifi) and your identity on websites has been around for a few years, standardised with the geolocation feature that I believe is part of HTML5 and accessed through javascript (on desktop browsers).
Its this combination of the wifi's geo-location and the fact that you were using this access point while logged into a website that allows the owners of a website to be able say
yes user "big rudy" was on our website and that he is the same person attached to the wifi access point "Toms wifi" located in the upstairs bedroom at 123 Main st, Surrey
(or wherever it is)
Basically its the technology that enables the dominoes pizza delivery guy to know your exact geo-location after you only have visited the dominoes website.
I'm not saying for sure this is what the BBC are doing to catch unauthorised users on their service but this is to me, the easiest and already "industry standardised" method IMHO.
This is quite an interesting question because at first I thought why don't the BBC request a lookup to the location API provided by the google street view cars?
Again assuming that they have decided to use this technique, Why bother going to all the trouble of doing what google have already done and made available for free? Then I realised, the reason for the vans, could be to bypass the do you allow this site/application to know your location? pop-over requirement the browsers impose on websites.
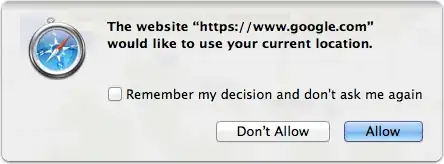
The popover is obviously so that you, the user, can decide if the website can know your location, it seems as though the BBC wish to deprive you of that right, but in order to do so, they will have to essentially recreate the geolocation platform that already exists and capture the wifi data themselves.
In case you weren't aware the google street view cars already have been sniffing encrypted wifi packets for a few years now.
Why do they sniff encrypted packets knowing that they will never get any info out of them? They don't want the info, they want the mac addresses and geo-location of the wifi access point. They get your wifi routers location through triangulation based on the strength of the wifi signal (i.e. the street view car is approaching your house and they see an essid of Toms wifi with a signal strength of x, they then make a note of that signal and its geo-location, they get a bit closer to your house and see the signal is now 2x they make a note of that, then as they go past it gets weaker, they turn a corner and if Toms wifi appears again, they keep updating their data, combine using simple trigonometry (triangulation) and now they have an accurate location of your - at this point - anonymous wifi access point.
Note: on mobile devices you generally don't need to go to all this work to get a users location, when its easier just to query the builtin GPS, but on laptops and desktops using wifi, the only other location revealing technique is ipaddress which would struggle to even predict your city with any accuracy.
The next piece is to reconcile your online identity with the wifi access point, I believe this is done by by using an "agent" i.e. a browser - which is already inside your otherwise private network, to query the MAC address of your access point (I suspect this is how its done, but I'm not sure - perhaps someone more knowledgeable could confirm/deny this?) a external service on the internet otherwise couldn't initiate a query/scan of your internal network - your network config wouldn't allow it)
At this point the "agent" (browser) is now capable of performing a lookup to google street view data API - which will then tell it the location of the wifi access point the computer/browser is connected to, then the browser avails this information to the web application via javascript.
Again, this is just my theory, but it seems to me this could be how BBC are tracking their users and why they need the vans.
