Technically, according to PCI SSC you can hold onto CVV and other sensitive authentication data until authorisation has occurred. In other words the restriction on storing sensitive authentication data applies to post authentication/processing storage.
Is it a requirement that the CVV be encrypted prior to authorisation?
-
While this should be answered by a QSA, there are answers on this similar thread which seem to apply here. https://security.stackexchange.com/questions/62334/storing-cvc-cvv-cvv2-until-payment-is-processed – user2320464 Jul 25 '16 at 16:15
2 Answers
The requirement is to protect the data appropriately. Pre-auth, you are unlikely to have the CVV on disk (it should just be in RAM) but if you do, then yes you should encrypt, and then delete afterwards, so your assumption that "the restriction on storing sensitive authentication data applies to post authentication/processing storage" is incorrect.
- 61,367
- 12
- 115
- 320
-
The only reason i can think of that a CVV would ever need to be stored on disk would be in a "store and forward" scenario, where the processor is not currently available to handle the transaction. – Bobson Jul 25 '16 at 19:17
-
As per PCI DSS you can not store cvv on disk. It is allowed to reside in RAM during online transaction and should be erased as soon as transaction finishes.
It is not required to encrypt CVV(itself being encrypted value) in switching from acquirer to issuer.
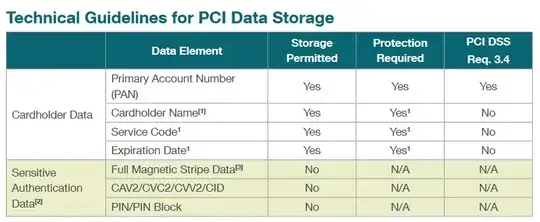
Refer to storage allowed and protection required fields below. for CVV storage not allowed and protection not applicable. Ref : https://www.pcisecuritystandards.org/pdfs/pci_fs_data_storage.pdf
- 101
- 3