What is the advantage of using jump servers for security reasons?
Jump servers, or more accurately, bastion hosts, provide a segregation layer between the target network and the user. Consider a network with database servers, application servers, an HSM or NAE for PCI, and monitoring systems. Without a bastion host, this needs to be exposed for maintenance and monitoring of these systems. The bastion host provides an auditable layer for users to access these systems. It also provides a separation of duties. Devops will need to access the servers, but Marketing typically won't need access.
Look at this basic network diagram without a bastion host:
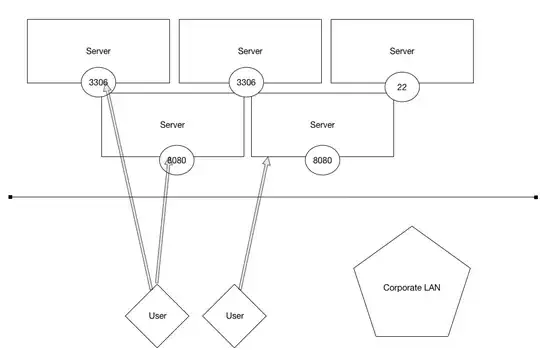
Any user on the network can access, and potentially attack, any server in that network. But by employing a bastion host, controls can be put in to place:
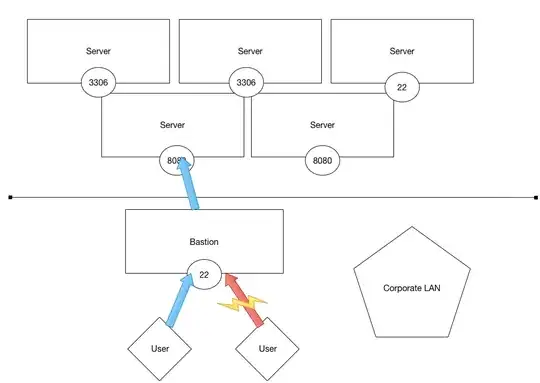
How can I use two-factor authentication with jump servers?
Check out libpam and configuration with TOTP.
Why do jump server need virtual machines?
They don't.

