Situation
We're wanting to use an HTTP logger/proxy/analyzer to inspect the access code, access token, and id token that are part of the code flow. The flow is happening among Google (the Authorization Server), a locally running web browser (the User Agent), and a locally running web application (the client).
What We've Tried #1
We've tried using Fiddler, WireShark, and RawCap and yet have not been able to view any of those. Here is an example of what we've tried.
- Start a RawCap session on our our IPv4 device.
rawcap -f 192.168.1.82 ipv4.pcaprawcap -f 127.0.0.1 loopback.pcap
- Go thru the code flow with the local web application and Google.
- Stop the RawCap session.
- Open the .pcap files in WireShark.
- View the packet list results and match them to the code flow steps.
Problem
All the communication between the local web application, Google, and the user agent appears hidden behind TLS. How can we view the codes and tokens? The Windows 10 loopback is always ::1 so RawCap doesn't capture it.
What We've Tried #2
Install WireShark.
Install Npcap. This is for capturing IPv6 loopback traffic on Windows 10.
Run the following in PowerShell. This sets an environmental variable, which tells Firefox and Chrome to log their pre-master secret to a file.
[System.Environment]::SetEnvironmentVariable("SSLKEYLOGFILE", "C:\Wireshark\sslkeylog.log", [System.EnvironmentVariableTarget]::Machine);
Restart Windows. You might not have to do this but doing so is thorough.
Start Wireshark.
- Configure SSL. Edit > Preferences > Protocols > SSL > (Pre)-Master-Secret log filename:
C:\Wireshark\sslkeylog.log - Start capture and include loopback. Capture > Options > Input. Choose both the
npcap Loopback AdapterandWi-Fi. - Set a display filter. The filter only displays SSL traffic between my computers and duckduckgo.com.
ssl and ip.dst == 192.168.1.82 and ip.src == 54.215.176.19. (Of course we can apply this to Google too.)
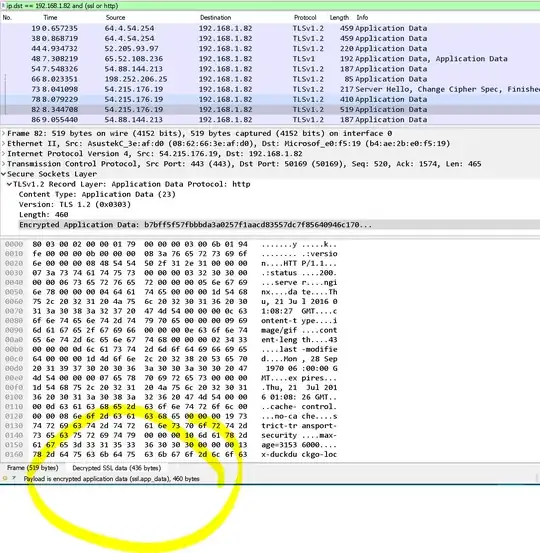
At this point, we will see the Decrypted SSL data (xxx bytes) tab in WireShark's Packet Bytes panel.
Export the Decrypted Data
- File > Export Packet Dissections > As Plain Text
- Packet Range > All Packets > Displayed
- Packet Format > Packet Bytes.
- File name > Whatever.txt
- Save as type > Plain text (*.txt)
- Save!
The resultant file will show each Frame and its Decrypted SSL Data. The decrypted data will unfortunately be in a hard-to-read columnar format.
See also
- https://www.wireshark.org/
- https://wiki.wireshark.org/CaptureSetup/Loopback
- https://wiki.wireshark.org/SSL
- https://jimshaver.net/2015/02/11/decrypting-tls-browser-traffic-with-wireshark-the-easy-way/
- Decrypting TLS in Wireshark when using DHE_RSA ciphersuites
- http://blog.davidvassallo.me/2010/08/04/exporting-saving-decrypted-data-from-wireshark/